The Importance of Cryptography for All of Us
Cryptography is crucial in the modern world due to the pervasive use of digital technology in many aspects of daily life, including communication (messengers), finance, and healthcare. It provides the means to secure data and ensure privacy, integrity, and authenticity in an environment where information can be easily intercepted, manipulated, or stolen. It helps to protect personal data and check data authenticity using encryption/decryption, device key authentication, and digital signatures.
The Challenge of a Post-Quantum Computing World
Post-quantum cryptography is about creating future-proof security methods that will be reliable and trustworthy even once quantum computers become available. The premise is that even those won’t be able to break post-quantum encryption within a reasonable and actionable timeframe.
The security of many encryption, data authentication and integrity methods used today, such as RSA and ECC (Elliptic Curve Cryptography), relies on the difficulty of solving certain mathematical problems, like integer factorization and discrete logarithms, which are computationally infeasible for classical computers to solve within any constrained time interval. This is what makes them practically unbreakable.
This is, however, about to change. Quantum computers will likely solve these problems more efficiently using Shor's Factoring Algorithm and other derived algorithms. These new algorithms can exponentially speed up the process of identifying the prime numbers used for RSA, ECC, and digital signature encryption. Suddenly, the common encryption methods we rely on for internet communication and sensitive data storage will be obsolete. Our data will no longer be secure.
Working on a Future-Proof Solution
Cryptography researchers are working on new types of security to counter the threat that the use of quantum computers and their ability to quickly solve certain types of mathematical problems could pose one day. The objective is clear: to develop new types of encryption and decryption-based security that don't rely on the math problems quantum computers are good at solving.
These new methods use different kinds of tough problems that even quantum computers would struggle with. Advanced lattice multiplication and hash-based algorithms are common approaches to staying ahead of the evolution of quantum computers.
Post-quantum algorithms are important and will become as important in the same varied set of use cases as traditional cryptography algorithms.
One such use case example that has already entered the real world is Apple*’s PQ3 post-quantum Cryptographic protocol, which is used with their iMessage* mobile messaging service.
NIST* collaborated with IDEMEA*, a French multinational technology company specializing in identity and authentication-related security services, to identify post-quantum protocols for banking applications and presented their recommendations at the 4th NIST PQC Standardization Conference. This work, as part of the NIST Post-Quantum Cryptography PQC in conjunction with many other contributions, led to the release of the first 3 NIST-backed Finalized Post-Quantum Encryption Standards.
Integrating post-quantum methods in the industry early, even before quantum computers become widely available, is necessary to establish forward secrecy. The threat of “retrospective decryption” refers to the ability to decrypt previously intercepted and recorded encrypted communications at a later point in time. We must assume that data encrypted using traditional methods will be collected and stored in anticipation of new decryption technology becoming available. To minimize that risk, it is good to establish a forward-looking security posture.
Figure 1 illustrates the ideal situation. Cryptography applications should start the transition to Postquantum Cryptography far before the first large quantum computers are built.
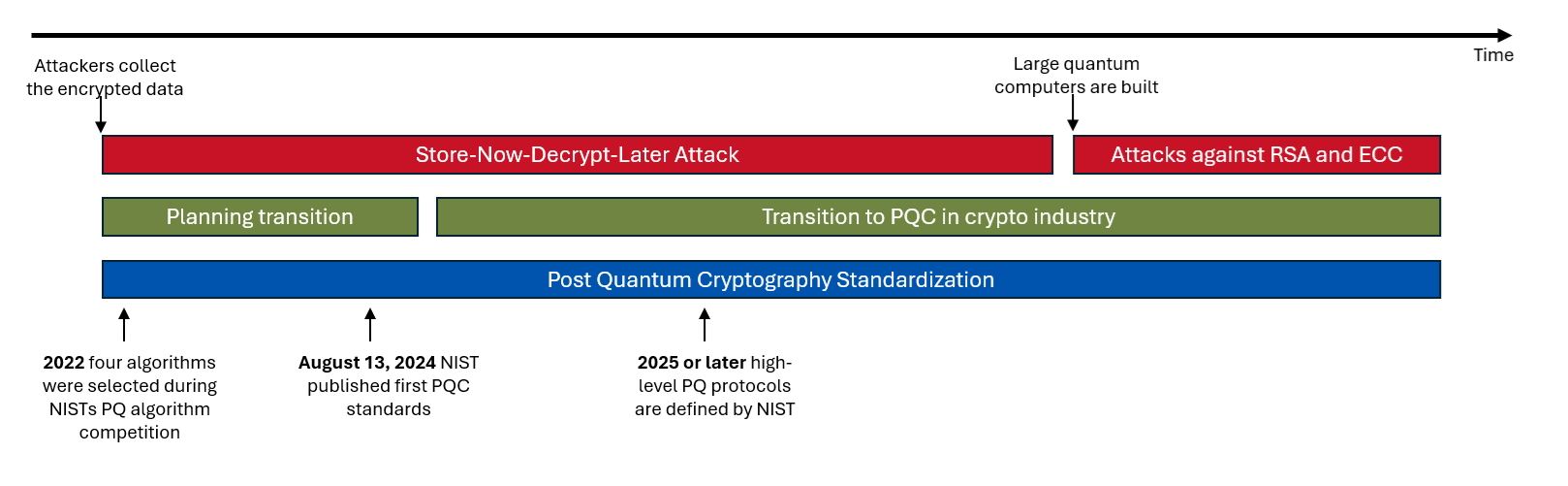
Figure 1: Post Quantum Cryptogrpahy Timeline
Since algorithms beyond the initial 3, selected during NISTs competition, are still under the active research, it is recommended to implement the transition in Hybrid mode. A “hybrid” is a combination of classical and post-quantum cryptography schemes.
For instance, to create a single Kyber512X key agreement, we can combine two cryptographic components:
- Kyber512, a post-quantum key encapsulation mechanism resistant to cryptanalytic and quantum computer attacks
- X25519, a classic cryptography key agreement scheme.
The advantage of using a hybrid is that the data remains secure against non-quantum attackers, even if Kyber512 turns out broken.
It is important to note that security is not just about the algorithm but also the implementation: Kyber512 might be perfectly secure, but an implementation might leak via side channels. The downside is that two key exchanges are performed, which takes more CPU cycles and bytes on the wire, but security is the first priority when we talk about Cryptography.
Overview of the Intel® Cryptography Primitives Library
The Intel Cryptography Primitives Library is a secure, fast, and lightweight library of cryptography building blocks, highly optimized for various Intel® CPUs (link to documentation).
It is available on GitHub.
Support for Many Cryptographic Domains
The library provides a comprehensive set of routines commonly used for cryptographic operations, including:

Benefits of Using the Intel Cryptography Primitives Library
- Security (constant-time execution for secret processing functions)
- Designed for the small footprint size
- Optimized for different Intel CPUs and instruction set architectures (including hardware cryptography instructions support):
- Intel® Streaming SIMD Extensions 2 (Intel® SSE2)
- Intel® SSE3
- Intel® SSE4.2
- Intel® Advanced Vector Extensions (Intel® AVX)
- Intel® Advanced Vector Extensions 2 (Intel® AVX2)
- Intel® Advanced Vector Extensions 512 (Intel® AVX-512)
- Configurable CPU dispatching for the best performance
- Kernel mode compatibility
- Thread-safe design
The Intel Cryptography Primitives Library supports building blocks (self-tests, services) for FIPS 140-3 compliance.
Post-quantum Cryptography Algorithms in the Intel® Cryptography Primitives Library
Currently, the Cryptography Primitives Library supports the verification of digital signatures: the eXtended Merkle Signature Scheme (XMSS) and Leighton-Micali Signature (LMS), which are stateful hash-based signature schemes. Both algorithms are standardized by NIST (NIST SP 800-208).
Note Unlike conventional digital signature schemes, stateful signature schemes require updating the secret key for every required signature check. For stateful hash-based signature schemes, signing requires keeping the state of the used one-time keys and ensuring they are never reused,
These algorithms are implemented as preview features in the Intel Cryptography Primitives Library. For additional details about preview features in the library, click here.
Using XMSS and LMS Cryptography
The Intel Cryptography Primitives Library documentation provides detailed examples for the use of both:
- XMSS Signature Verification Scheme
- LMS Signature Verification
The library implementations provide special functions like getters and setters that are required to call algorithms.
Comparing ECDSA and LMS Verification Usage
Here is an example comparing the use of Intel Cryptography Primitives Library implementations of Elliptic Curve Digital Signature Authority (ECDSA) verification and Leighton-Micali Signature (LMS) verification schemes:
|
|
Figure 2: Comparison of ECDSA and LMS Verification Scheme
Note:
Check out the Detailed LMS Usage Example on the Intel Cryptography Primitives Library Github
Add Post Quantum Security to Your Application
The Intel Cryptography Primitives Library provides Post-Quantum Security already today with its support for XMSS (eXtended Merkle Signature Scheme) and LMS Leighton-Micali Signature hash-based cryptography schemes.
We are at the forefront of implementing the latest in post-quantum cryptographic technology and are closely monitoring the evolution of standards at NIST’s Post Quantum Cryptography PQC.
Join us in making our sensitive, critical data and future more secure.
Download the Intel Cryptography Primitives Library standalone or as part of the Intel® oneAPI Base Toolkit.
If you have any questions or requests to extend the list of post-quantum algorithms, please submit the issue on Github or in the online service center.
We are looking forward to your feedback and suggestions.
Additional Resources
Tutorials
- Exceed FIPS 140 Level Information Security with Intel Cryptography Primitives Library
- AES-GCM Acceleration with Intel® Cryptography Primitives Library
- Cryptography Code Samples
NIST Post-Quantum Cryptography Standardization
Post Quantum Encryption with Intel Cryptography Primitives Library
- Post-quantum Algorithms in Intel® Cryptography Primitives Library
- eXtended Merkle Signature Scheme (XMSS)
-
Leighton-Micali Hash-Based Signatures (LMS)