With the exponential growth of data and data-centric business processes, developers face enormous challenges to make information more secure at scale. With Intel® Security Libraries for Data Centers (Intel® SecL-DC), developers can take advantage of a hardware foundation of trust for their Intel-based platforms and solutions, making better security easier to build into a broader range of solutions, maintaining high performance as they help protect data at rest, data in motion, and data in process.

Integrate & Deploy Hardware-Enhanced Security at Scale
Developers that continue to use software-only security capabilities should not expect different results year after year. A multi-layered, defense-in-depth approach should begin with a hardware-based foundation of trust forming the basis for helping secure the solutions. So, we innovate to enable technologies to improve protection of the platform from power-on up through the stack of hypervisor, virtual machines (VMs), operating systems (OSs), and applications.
The value hackers seek is in the data— whether it’s at rest, in flight, or in use. Whatever solutions are delivered to increase trust and help protect data, they should not compromise productivity and performance. Some organizations may hesitate to introduce critical capabilities for protection out of concern that security solutions may slow down business processes, but increased protection and productivity are not mutually exclusive. Hardware-enhanced security can help mitigate that concern.
| HyTrust* Boundary Controls Helps Ensure Data Geo-Location Compliance In a multi-cloud world where security often plays catchup, organizations face compliance challenges in several areas, including how they manage the geo-location of customer data they process and store. Using Intel SecL-DC, HyTrust developed a solution to help ensure data can only be decrypted in specific geo-locations. It provides advanced privileged user access control, policy enforcement, forensic and automated compliance for private clouds. According Patrick Conte, HyTrust Senior VP, Global Business Development, “HyTrust CloudControl and other HyTrust platforms leverage Intel SecL-DC components to enable Intel TXT and TPM for geo-fencing of critical workloads. Called Boundary Controls, this solution allows customers to tag workloads to specific physical servers in their private or hybrid clouds, and only execute if they get a ‘root of trust’ from the underlying, trusted hardware. This unique solution was built jointly by HyTrust and Intel."
|
Hardware, software, policy and processes work together for the best results. The various layers of management and software stacks require consistent ways to discover, attest, and utilize hardware-based security. That is why Intel is launching Intel Security Libraries for Data Centers (Intel SecL-DC) in conjunction with the release of 2nd Gen Intel® Xeon® Scalable processors—to provide consistent interfaces that programmatically enable automation and improve data protection.
Intel SecL-DC is designed to make hardware-based data center security much easier to build into a broad range of solutions and more effective against bad actors. To simplify the integration and deployment of Intel® hardware-based security technologies at scale, Intel SecL-DC brings optimized programming interfaces and management tools for many Intel® security technologies together into one easier-to-use set of libraries and tools. This approach provides stronger security as compared to software-only solutions because features such as Intel® Trusted Execution Technology (Intel® TXT) and trusted platform module (TPM 2.0) are rooted in Intel® silicon.
The Intel SecL-DC software is open sourced and ready to integrate into your data center solutions. For example, orchestration software can evaluate the security assertions provided by Intel SecL-DC to control the placement and migration of workloads on the various data center and cloud availability zones.
With Intel SecL-DC and 2nd Gen Intel Xeon Scalable processors, developers can take advantage of software optimizations combined with hardware support for the strong algorithms and strong keys that are essential to strong cryptography. These software and hardware technologies lay the foundation for security-related solutions while maintaining high performance across data at rest, data in motion, and data in process.
In addition, we recently announced the release of Intel® Threat Detection Technology (Intel® TDT) for datacenter and cloud. It includes support for virtualized Linux* environments and integration with Intel SecL-DC. Intel TDT uses platform telemetry and machine learning to assist security software in improved detection of targeted threats such as crypto-mining attacks. Hardware enhanced detection by Intel TDT can lead to better efficacy, lower performance overhead and lower false positives when integrated with leading security solutions.
Get Started Today
Take the next step and identify where you can use Intel TDT and Intel SecL-DC in your next project.
- Download Intel SecL-DC at GitHub.
- Visit intel.com for more information on Intel TDT now, and stay informed on additional innovations soon to come.
Related Content
Intel® Security Libraries for Data Center [Beta]: A set of building blocks that discover, attest, and utilize Intel security features to enable critical cloud security and confidential computing use-cases.
Intel® Hardware-Enabled Security: Boost protection against evolving and modern threats.
Intel Unveils New Technologies to Accelerate Innovation in a Data-Centric World: Next-generation technologies enable the accelerated movement, storage and processing of the world’s data
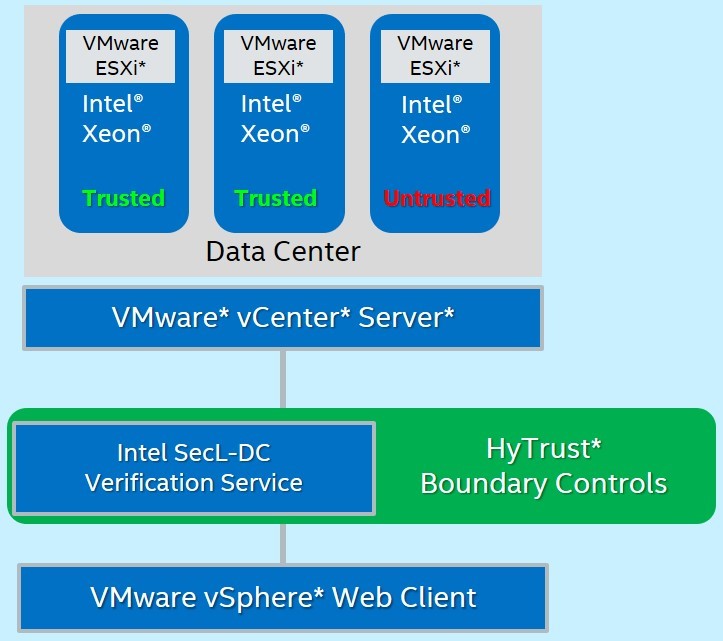 The HyTrust solution works with VMware* vCenter* to provide a quote of boot-time platform measurements from each server TPM to the Intel SecL-DC Verification Service. Intel SecL-DC Verification Service compares measured results against stored expected values and verifies hardware-based geo-location tags. Servers are then categorized as “trusted” or “untrusted” based on measurements. The HyTrust Boundary Controls solution assigns policies to each VM based on trusted status and geo-location tags, and it will prevent user actions (like migrations) from violating those policies.
The HyTrust solution works with VMware* vCenter* to provide a quote of boot-time platform measurements from each server TPM to the Intel SecL-DC Verification Service. Intel SecL-DC Verification Service compares measured results against stored expected values and verifies hardware-based geo-location tags. Servers are then categorized as “trusted” or “untrusted” based on measurements. The HyTrust Boundary Controls solution assigns policies to each VM based on trusted status and geo-location tags, and it will prevent user actions (like migrations) from violating those policies.