“The security of our products is one of our most important priorities. We strive to design, manufacture, and sell the world's most secure technology products, and we are continuously innovating and enhancing security capabilities for our products.”1
– Pat Gelsinger, Intel CEO
The history of computer security involves cooperation and synergy between hardware and software. As processors are released with new security features, software is modified to take advantage of them. As software releases new security features, processors advance to accelerate these features and give software the next set of features to allow it to push even further. Intel has a long history of bringing innovative security features to its processors and a system-on-a-chip (SoC). Intel's recent client and server processors continue this security tradition by delivering the next generation of new and exciting features. Security begins with Intel.
Long before "confidential computing" was a buzzword, Intel introduced Intel® Software Guard Extensions (Intel® SGX). First released in the 6th generation Intel® Core™ processors, Intel SGX allows software developers to create applications with the smallest available attack surface (one that doesn’t fully depend on the underlying operating system). The following figure depicts the role of Intel SGX:
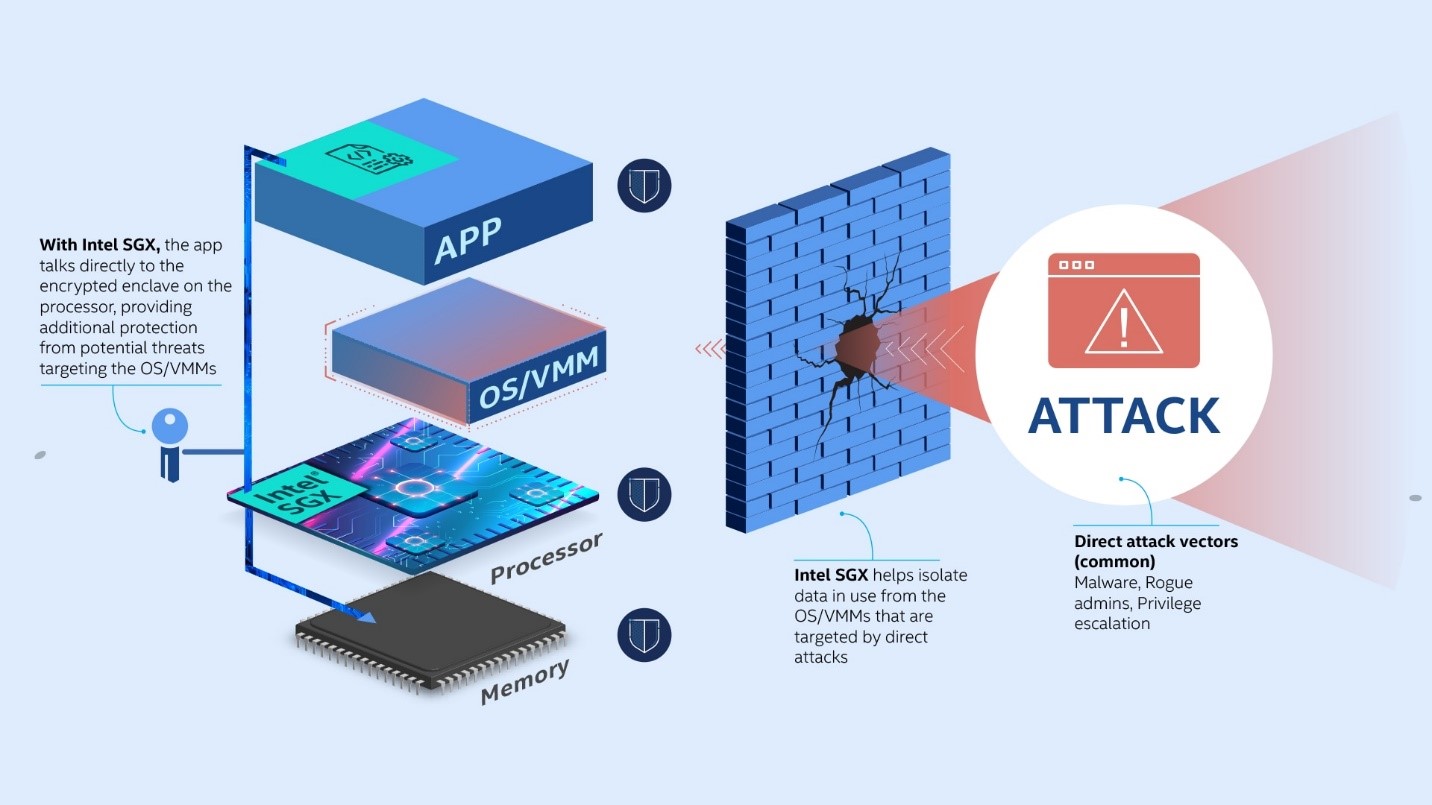
Image source: Understand Intel® SGX.
Intel brought Intel SGX to the server and data center market with the 3rd generation Intel® Xeon® Scalable processor. Enterprises and Cloud Service Providers (CSP) can build and deliver solutions with a new and unparalleled level of security that simply wasn’t possible before. Recognizing the value of Intel SGX, Microsoft Azure* has supported confidential computing with Intel SGX since 2017.2 This new line of processors offers notable upgrades to Azure virtual machines (VM) that are capable of using Intel SGX.3
Intel extended support for confidential computing to virtualized environments with Intel® Total Memory Encryption – Multi-Key (Intel® TME-MK). Introduced on the 3rd generation Intel Xeon Scalable processor and 12th generation Intel Core processors, Intel TME-MK extends the encryption used to help protect user data on disks and in file systems to the system main memory and VMs by supporting multiple, hardware-generated keys. This allows hypervisors to separately encrypt the memory of each VM, further isolating and better protecting it from various physical attacks or attacks from other VMs—protection that would not be possible with software alone. This capability is now offered in the new Intel®-based DCsv3 series of confidential VMs4 available in Azure and in the Azure Stack Hyperconverged Infrastructure (HCI), version 21H2.
Intel continues to lead and innovate in confidential computing by releasing the Intel® Trust Domain Extensions (Intel® TDX) specification.5 Intel TDX builds on the per-VM encryption capabilities of Intel TME-MK to extend the security model of Intel SGX from the application space to the entire VM. This helps cloud tenants isolate guest operating systems and their entire software stack from the underlying hypervisor and host operating system. It will be possible to give off-the-shelf workloads some of the industry's strongest trust properties.
Intel® Control-Flow Enforcement Technology (Intel® CET) debuted with the 11th generation Intel® Core™ mobile processors. As shown in the following figure, Intel CET helps protect against the entire class of software exploits known as: return-, call-, and jump-oriented programming (ROP, COP, JOP).
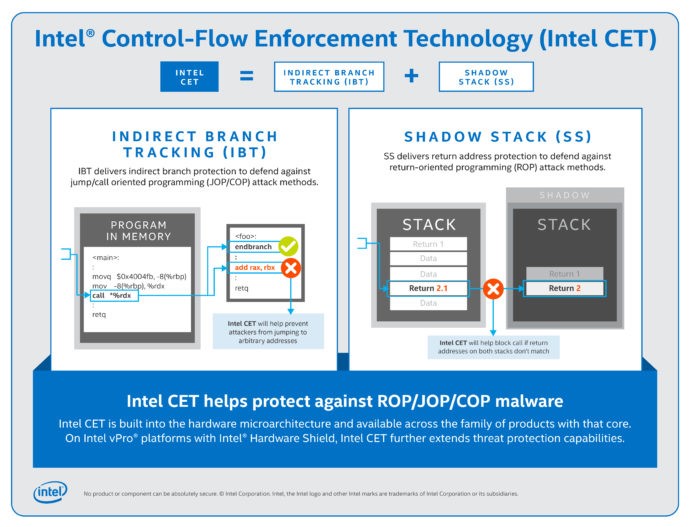
Image source: Intel CET Answers Call to Protect Against Common Malware Threats.
These attacks have existed since the “return-to-libc” exploit in 1997 and have not been possible to mitigate efficiently with just software. ROP attacks are some of the most common attacks across all operating systems and applications. Windows* 11 and newer versions of Windows® 10 support Intel CET to harden the operating system and applications that run on it.6 Microsoft Edge* and Chrome*, two of today's most used applications, now have Intel CET support.
Intel® Threat Detection Technology (Intel® TDT), which is part of Intel® vPro® Security, is a software development kit (SDK) that uses advanced AI algorithms to interpret data provided by hardware monitors embedded in the 11th and later generation Intel Core processors. These monitors tell Intel TDT how various software is performing. In response, Intel TDT AI routines use that data to help distinguish between normal user activities and malware, such as cryptominers and ransomware. Intel TDT also uses the GPU in SoCs from Intel to accelerate AI inferencing and reduce CPU overhead. Cryptomining detection in Intel TDT has been integrated into Microsoft* Defender for Endpoint,7 which is part of every Windows 10 and Windows 11 installation. Cybereason* is the first of several security independent software vendors (ISV) to announce support for Intel TDT ransomware protection capabilities.8
Intel® Trusted Execution Technology (Intel® TXT) has been available on Intel Xeon platforms since 2010 and on Intel vPro® technology clients since 2007. Industry leaders such as HyTrust*, Citrix*, VMware*, and the Linux* kernel9 have also adopted it. But the adoption of Intel TXT by Windows as part of the Secured-core PC and server initiatives brought Intel TXT into the mainstream. Intel TXT has enabled Microsoft* to help reduce the attack surface of its operating systems and hypervisors, further hardening its boot process. The first Secured-core servers, based on 3rd generation Intel Xeon Scalable processors, are available in the Azure Stack HCI and Windows Server* catalogs.10 Though Secured-core PCs have been available since 2019, Intel has continued to extend protections based on Intel TXT by using the Intel vPro® Security “below-the-operating-system” security, which isolates code in the platform BIOS System Management Mode (SMM) to further aid in protecting the operating system. This support is now also part of the Secured-core PC requirements.11
Starting with Intel 11th generation Intel Core processors, Windows Hello* Enhanced Sign-in Security is available for face recognition.12 Windows uses a USB dual-channel hardware capability from Intel to more securely route the camera data to the VBS-protected facial recognition process, while still allowing performant concurrent use of all the other USB devices on the system.13
Cryptography is part of almost everything users do online and on their PCs. It protects their data on hard drives, pictures in the cloud, and credit card information as it is sent to websites. With the 3rd generation Intel Xeon Scalable processor, Intel added instructions to accelerate this protection and software support and guidance to maximize performance. These instructions speed up the AES algorithm used for data encryption and help improve the performance of SHA and public-key cryptography used for authenticating internet transactions, as depicted in the following figure.
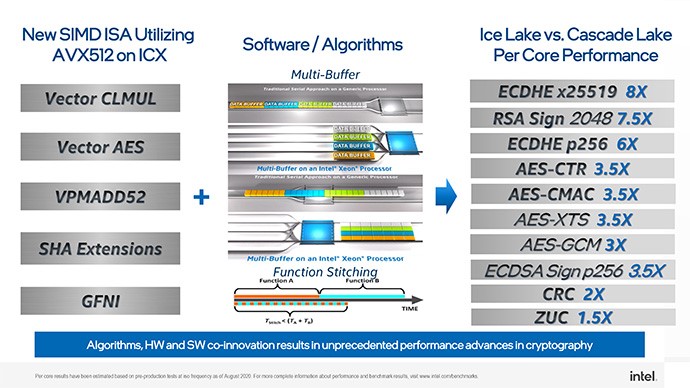
For more information, see Crypto Acceleration: Enabling a Path to the Future of Computing.
Intel has published several papers detailing innovative ways to optimize software to take advantage of these new instructions. It has also added support to many of the most popular cryptographic libraries, such as OpenSSL* and Intel® Integrated Performance Primitives, to transparently help improve the performance of software.14 The Azure Stack HCI, version 21H2 supports these new instructions.
The 12th generation Intel Core processors contain a new technology, Intel® Virtualization Technology - Redirect Protection (Intel® VT-rp) that can help protect operating systems from rootkits. While it's not in any operating system today, Intel VT-rp will help future operating systems protect themselves against some of the most advanced malware techniques that manipulate page tables to stealthily take control of a platform, often undetected by software.
As our CEO has said, Intel is setting a torrid pace in all that we do, and security is no exception. Security attacks, which are increasing in both pace and sophistication, target almost everything that computes: from online purchases to bank accounts, PCs to servers and even cars, businesses from the local flower shop to Fortune 500 companies, critical infrastructure such as water treatment plants and electricity generation. Yesterday's protections won't prevent tomorrow's attacks. The suite of security technologies in the newest Intel products, combined with the industry's latest software solutions, can help to protect against these sophisticated attacks wherever they're launched. Intel continues to deliver new security features and technologies while working with the rest of the computing ecosystem to ensure that new solutions bring real value to businesses and users.
References
2 Introducing Azure Confidential Computing
3 Azure Announces the Next-Generation Intel SGX Confidential Computing VMs
4 Key Foundations for Protecting Your Data with Azure Confidential Computing
6 Developer Guidance for Hardware-Enforced Stack Protection
7 Defending against Cryptojacking with Microsoft Defender for Endpoint and Intel TDT
8 Cybereason and Intel Introduce Hardware-Enabled Ransomware Protections for Businesses
9 Trusted Execution Technology
11 Detailed Information on System Management Mode (SMM): How SMM Isolation Hardens the Platform
12 Windows Hello Enhanced Sign-in Security
13 Intel® Virtualization Technology: Help Protect Endpoint Applications
14 Cryptographic Acceleration: Enable a Path to the Future of Computing