One question about Intel® Software Guard Extensions (Intel® SGX) that comes up frequently is how to mix enclaves with managed code on Microsoft Windows* platforms, particularly with the C# language. While enclaves themselves must be 100 percent native code and the enclave bridge functions must be 100 percent native code with C (and not C++) linkages, it is possible, indirectly, to make an ECALL into an enclave from .NET and to make an OCALL from an enclave into a .NET object. There are multiple solutions for accomplishing these tasks, and this article and its accompanying code sample demonstrate one approach.
Mixing Managed Code and Native Code with C++/CLI
Microsoft Visual Studio* 2005 and later offers three options for calling unmanaged code from managed code:
- Platform Invocation Services, commonly referred to by developers as P/Invoke
- COM
- C++/CLI
P/Invoke is good for calling simple C functions in a DLL, which makes it a reasonable choice for interfacing with enclaves, but writing P/Invoke wrappers and marshaling data can be difficult and error-prone. COM is more flexible than P/Invoke, but it is also more complicated; that additional complexity is unnecessary for interfacing with the C bridge functions required by enclaves. This code sample uses the C++/CLI approach.
C++/CLI offers significant convenience by allowing the developer to mix managed and unmanaged code in the same module, creating a mixed-mode assembly which can in turn be linked to modules comprised entirely of either managed or native code. Data marshaling in C++/CLI is also fairly easy: for simple data types it is done automatically through direct assignment, and helper methods are provided for more complex types such as arrays and strings. Data marshaling is, in fact, so painless in C++/CLI that developers often refer to the programming model as IJW (an acronym for “it just works”).
The trade-off for this convenience is that there can be a small performance penalty due to the extra layer of functions, and it does require that you produce an additional DLL when interfacing with Intel SGX enclaves.
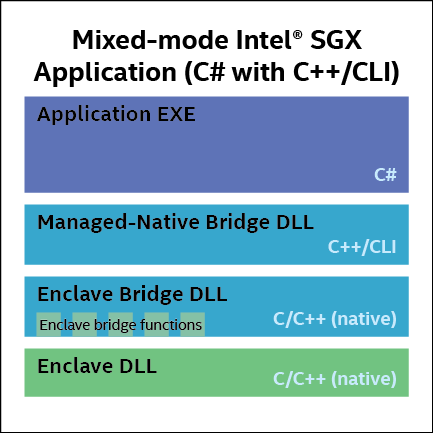
Figure 1 Minimum component makeup of an Intel® Software Guard Extensions application written in C# and C++/CLI.
Figure 1 illustrates the component makeup of a C# application when using the C++/CLI model. The managed application consists of, at minimum, a C# executable, a C++/CLI DLL, the native enclave bridge DLL, and the enclave DLL itself.
The Sample Application
The sample application provides two functions that execute inside of an enclave: one calls CPUID, and the other generates random data in 1KB blocks and XORs them together to produce a final 1KB block of random bytes. This is a multithreaded application, and you can run all three tasks simultaneously. The user interface is shown in Figure 2.
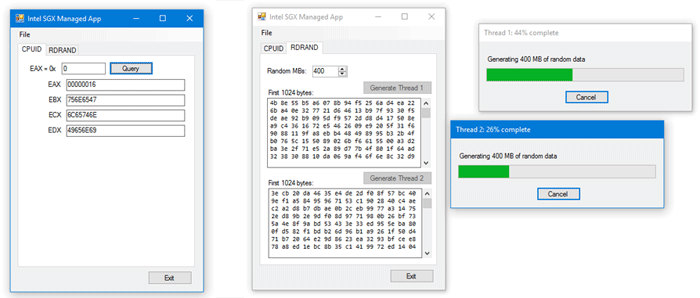
Figure 2: Sample application user interface.
To build the application you will need the Intel SGX SDK. This sample was created using the 1.6 Intel SGX SDK and built with Microsoft Visual Studio 2013. It targets the .NET framework 4.5.1.
The CPUID Tab
On the CPUID panel, you enter a value for EAX to pass to the CPUID instruction. When you click query, the program executes an ECALL on the current thread and runs the sgx_cpuid() function inside the enclave. Note that sgx_cpuid() does, in turn, make an OCALL to execute the CPUID instruction, since CPUID is not a legal instruction inside an enclave. This OCALL is automatically generated for you by the edgr8tr tool when you build your enclave. See the Intel SGX SDK Developer Guide for more information on the sgx_cpuid() function.
The RDRAND Tab
On the RDRAND panel you can generate up to two simultaneous background threads. Each thread performs the same task: it makes an ECALL to enter the enclave and generates the target amount of random data using the sgx_read_rand() function in 1 KB blocks. Each 1 KB block is XORd with the previous block to produce a final 1 KB block of random data that is returned to the application (the first block is XORd with a block of 0s).
For every 1 MB of random data that is generated, the function also executes an OCALL to send the progress back up to the main application via a callback. The callback function then runs a thread in the UI context to update the progress bar.
Because this function runs asynchronously, you can have both threads in the UI active at once and even switch to the CPUID tab to execute that ECALL while the RDRAND ECALLs are still active.
Overall Structure
The application is made up of the following components, three of which we’ll examine in detail:
- C# application. A Windows Forms*-based application that implements the user interface.
- EnclaveLink.dll. A mixed-mode DLL responsible for marshaling data between .NET and native code. This assembly contains two classes: EnclaveLinkManaged and EnclaveLinkNative.
- EnclaveBridge.dll. A native DLL containing the enclave bridge functions. These are pure C functions.
- Enclave.dll (Enclave.signed.dll). The Intel SGX enclave.
There is also a fifth component, sgx_support_detect.dll, which is responsible for the runtime check of Intel SGX capability. It ensures that the application exits gracefully when run on a system that does not support Intel SGX. We won’t be discussing this component here, but for more information on how it works and why it’s necessary, see the article Properly Detecting Intel® Software Guard Extensions in Your Applications.
The general application flow is that the enclave is not created immediately when the application launches. It initializes some global variables for referencing the enclave and creates a mutex. When a UI event occurs, the first thread that needs to run an enclave function checks to see if the enclave has already been created, and if not, it launches the enclave. All subsequent threads and events reuse that same enclave. In order to keep the sample application architecture relatively simple, the enclave is not destroyed until the program exits.
The C# Application
The main executable is written in C#. It requires a reference to the EnclaveLink DLL in order to execute the C/C++ methods that eventually call into the enclave.
On startup, the application calls static methods to prepare the application for the enclave, and then closes it on exit:
public FormMain()
{
InitializeComponent();
// This doesn't create the enclave, it just initializes what we need
// to do so in an multithreaded environment.
EnclaveLinkManaged.init_enclave();
}
~FormMain()
{
// Destroy the enclave (if we created it).
EnclaveLinkManaged.close_enclave();
}These two functions are simple wrappers around functions in EnclaveLinkNative and are discussed in more detail below.
When either the CPUID or RDRAND functions are executed via the GUI, the application creates an instance of class EnclaveLinkManaged and executes the appropriate method. The CPUID execution flow is shown, below:
private void buttonCPUID_Click(object sender, EventArgs e)
{
int rv;
UInt32[] flags = new UInt32[4];
EnclaveLinkManaged enclave = new EnclaveLinkManaged();
// Query CPUID and get back an array of 4 32-bit unsigned integers
rv = enclave.cpuid(Convert.ToInt32(textBoxLeaf.Text), flags);
if (rv == 1)
{
textBoxEAX.Text = String.Format("{0:X8}", flags[0]);
textBoxEBX.Text = String.Format("{0:X8}", flags[1]);
textBoxECX.Text = String.Format("{0:X8}", flags[2]);
textBoxEDX.Text = String.Format("{0:X8}", flags[3]);
}
else
{
MessageBox.Show("CPUID query failed");
}
}The callbacks for the progress bar in the RDRAND execution flow are implemented using a delegate, which creates a task in the UI context to update the display. The callback methodology is described in more detail later.
Boolean cancel = false;
progress_callback callback;
TaskScheduler uicontext;
public ProgressRandom(int mb_in, int num_in)
{
enclave = new EnclaveLinkManaged();
mb = mb_in;
num = num_in;
uicontext = TaskScheduler.FromCurrentSynchronizationContext();
callback = new progress_callback(UpdateProgress);
InitializeComponent();
labelTask.Text = String.Format("Generating {0} MB of random data", mb);
}
private int UpdateProgress(int received, int target)
{
Task.Factory.StartNew(() =>
{
progressBarRand.Value = 100 * received / target;
this.Text = String.Format("Thread {0}: {1}% complete", num, progressBarRand.Value);
}, CancellationToken.None, TaskCreationOptions.None, uicontext);
return (cancel) ? 0 : 1;
}The EnclaveLink DLL
The primary purpose of the EnclaveLink DLL is to marshal data between .NET and unmanaged code. It is a mixed-mode assembly that contains two objects:
- EnclaveLinkManaged, a managed class that is visible to the C# layer
- EnclaveLinkNative, a native C++ class
EnclaveLinkManaged contains all of the data marshaling functions, and its methods have variables in both managed and unmanaged memory. It ensures that only unmanaged pointers and data get passed to EnclaveLinkNative. Each instance of EnclaveLinkManaged contains an instance of EnclaveLinkNative, and the methods in EnclaveLinkManaged are essentially wrappers around the methods in the native class.
EnclaveLinkNative is responsible for interfacing with the enclave bridge functions in the EnclaveBridge DLL. It also is responsible for initializing the global enclave variables and handling the locking.
#define MUTEX L"Enclave"
static sgx_enclave_id_t eid = 0;
static sgx_launch_token_t token = { 0 };
static HANDLE hmutex;
int launched = 0;
void EnclaveLinkNative::init_enclave()
{
hmutex = CreateMutex(NULL, FALSE, MUTEX);
}
void EnclaveLinkNative::close_enclave()
{
if (WaitForSingleObject(hmutex, INFINITE) != WAIT_OBJECT_0) return;
if (launched) en_destroy_enclave(eid);
eid = 0;
launched = 0;
ReleaseMutex(hmutex);
}
int EnclaveLinkNative::get_enclave(sgx_enclave_id_t *id)
{
int rv = 1;
int updated = 0;
if (WaitForSingleObject(hmutex, INFINITE) != WAIT_OBJECT_0) return 0;
if (launched) *id = eid;
else {
sgx_status_t status;
status= en_create_enclave(&token, &eid, &updated);
if (status == SGX_SUCCESS) {
*id = eid;
rv = 1;
launched = 1;
} else {
rv= 0;
launched = 0;
}
}
ReleaseMutex(hmutex);
return rv;
}The EnclaveBridge DLL
As the name suggests, this DLL holds the enclave bridge functions. This is a 100 percent native assembly with C linkages, and the methods from EnclaveLinkNative call into these functions. Essentially, they marshal data and wrap the calls in the mixed mode assembly to and from the enclave.
The OCALL and the Callback Sequence
The most complicated piece of the sample application is the callback sequence used by the RDRAND operation. The OCALL must propagate from the enclave all the way up the application to the C# layer. The task is to pass a reference to a managed class instance method (a delegate) down to the enclave so that it can be invoked via the OCALL. The challenge is to do that within the following restrictions:
- The enclave is in its own DLL, which cannot depend on other DLLs.
- The enclave only supports a limited set of data types.
- The enclave can only link against 100 percent native functions with C linkages.
- There cannot be any circular DLL dependencies.
- The methodology must be thread-safe.
- The user must be able to cancel the operation.
The Delegate
The delegate is prototyped inside of EnclaveLinkManaged.h along with the EnclaveLinkManaged class definition:
public delegate int progress_callback(int, int);
public ref class EnclaveLinkManaged
{
array<BYTE> ^rand;
EnclaveLinkNative *native;
public:
progress_callback ^callback;
EnclaveLinkManaged();
~EnclaveLinkManaged();
static void init_enclave();
static void close_enclave();
int cpuid(int leaf, array<UINT32>^ flags);
String ^genrand(int mb, progress_callback ^cb);
// C++/CLI doesn't support friend classes, so this is exposed publicly even though
// it's only intended to be used by the EnclaveLinkNative class.
int genrand_update(int generated, int target);
};When each ProgressRandom object is instantiated, a delegate is assigned in the variable callback, pointing to the UpdateProgress instance method:
public partial class ProgressRandom : Form
{
EnclaveLinkManaged enclave;
int mb;
Boolean cancel = false;
progress_callback callback;
TaskScheduler uicontext;
int num;
public ProgressRandom(int mb_in, int num_in)
{
enclave = new EnclaveLinkManaged();
mb = mb_in;
num = num_in;
uicontext = TaskScheduler.FromCurrentSynchronizationContext();
callback = new progress_callback(UpdateProgress);
InitializeComponent();
labelTask.Text = String.Format("Generating {0} MB of random data", mb);
}This variable is passed as an argument to the EnclaveLinkManaged object when the RDRAND operation is requested:
public Task<String> RunAsync()
{
this.Refresh();
// Create a thread using Task.Run
return Task.Run<String>(() =>
{
String data;
data= enclave.genrand(mb, callback);
return data;
});
}The genrand() method inside of EnclaveLinkManaged saves this delegate to the property “callback”. It also creates a GCHandle that both points to itself and pins itself in memory, preventing the garbage collector from moving it in memory and thus making it accessible from unmanaged memory. This handle is passed as a pointer to the native object.
This is necessary because we cannot directly store a handle to a managed object as a member of an unmanaged class.
String ^EnclaveLinkManaged::genrand(int mb, progress_callback ^cb)
{
UInt32 rv;
int kb= 1024*mb;
String ^mshex = gcnew String("");
unsigned char *block;
// Marshal a handle to the managed object to a system pointer that
// the native layer can use.
GCHandle handle= GCHandle::Alloc(this);
IntPtr pointer= GCHandle::ToIntPtr(handle);
callback = cb;
block = new unsigned char[1024];
if (block == NULL) return mshex;
// Call into the native layer. This will make the ECALL, which executes
// callbacks via the OCALL.
rv= (UInt32) native->genrand(kb, pointer.ToPointer(), block);
In the native object, we now have a pointer to the managed object, which we save in the member variable managed.
Next, we use a feature of C++11 to create a std::function reference that is bound to a class method. Unlike standard C function pointers, this std::function reference points to the class method in our instantiated object, not to a static or global function.
DWORD EnclaveLinkNative::genrand (int mkb, void *obj, unsigned char rbuffer[1024])
{
using namespace std::placeholders;
auto callback= std::bind(&EnclaveLinkNative::genrand_progress, this, _1, _2);
sgx_status_t status;
int rv;
sgx_enclave_id_t thiseid;
if (!get_enclave(&thiseid)) return 0;
// Store the pointer to our managed object as a (void *). We'll Marshall this later.
managed = obj;
// Retry if we lose the enclave due to a power transition
again:
status= en_genrand(thiseid, &rv, mkb, callback, rbuffer);Why do we need this layer of indirection? Because the next layer down, EnclaveBridge.dll, cannot have a linkage dependency on EnclaveLink.dll as this would create a circular reference (where A depends on B, and B depends on A). EnclaveBridge.dll needs an anonymous means of pointing to our instantiated class method.
Inside en_genrad() in EnclaveBridge.cpp, this std::function is converted to a void pointer. Enclaves only support a subset of data types, and they don’t support any of the C++11 extensions regardless. We need to convert the std::function pointer to something the enclave will accept. In this case, that means passing the pointer address in a generic data buffet. Why use void instead of an integer type? Because the size of a std::function pointer varies by architecture.
typedef std::function<int(int, int)> progress_callback_t;
ENCLAVENATIVE_API sgx_status_t en_genrand(sgx_enclave_id_t eid, int *rv, int kb, progress_callback_t callback, unsigned char *rbuffer)
{
sgx_status_t status;
size_t cbsize = sizeof(progress_callback_t);
// Pass the callback pointer to the enclave as a 64-bit address value.
status = e_genrand(eid, rv, kb, (void *)&callback, cbsize, rbuffer);
return status;
}Note that we not only must allocate this data buffer, but also tell the edgr8r tool how large the buffer is. That means we need to pass the size of the buffer in as an argument, even though it is never explicitly used.
Inside the enclave, the callback parameter literally just gets passed through and out the OCALL. The definition in the EDL file looks like this:
enclave {
from "sgx_tstdc.edl" import *;
trusted {
/* define ECALLs here. */
public int e_cpuid(int leaf, [out] uint32_t flags[4]);
public int e_genrand(int kb, [in, size=sz] void *callback, size_t sz, [out, size=1024] unsigned char *block);
};
untrusted {
/* define OCALLs here. */
int o_genrand_progress ([in, size=sz] void *callback, size_t sz, int progress, int target);
};
};The callback starts unwinding in the OCALL, o_genrand_progress:
typedef std::function<int(int, int)> progress_callback_t;
int o_genrand_progress(void *cbref, size_t sz, int progress, int target)
{
progress_callback_t *callback = (progress_callback_t *) cbref;
// Recast as a pointer to our callback function.
if (callback == NULL) return 1;
// Propogate the cancellation condition back up the stack.
return (*callback)(progress, target);
}The callback parameter, cbref, is recast as a std::function binding and then executed with our two arguments: progress and target. This points back to the genrand_progress() method inside of the EnclaveLinkNative object, where the GCHandle is recast to a managed object reference and then executed.
int __cdecl EnclaveLinkNative::genrand_progress (int generated, int target)
{
// Marshal a pointer to a managed object to native code and convert it to an object pointer we can use
// from CLI code
EnclaveLinkManaged ^mobj;
IntPtr pointer(managed);
GCHandle mhandle;
mhandle= GCHandle::FromIntPtr(pointer);
mobj= (EnclaveLinkManaged ^)mhandle.Target;
// Call the progress update function in the Managed version of the object. A retval of 0 means
// we should cancel our operation.
return mobj->genrand_update(generated, target);
}The next stop is the managed object. Here, the delegate that was saved in the callback class member is used to call up to the C# method.
int EnclaveLinkManaged::genrand_update(int generated, int target)
{
return callback(generated, target);
}This executes the UpdateProgress() method, which updates the UI. This delegate returns an int value of either 0 or 1, which represents the status of the cancellation button:
private int UpdateProgress(int received, int target)
{
Task.Factory.StartNew(() =>
{
progressBarRand.Value = 100 * received / target;
this.Text = String.Format("Thread {0}: {1}% complete", num, progressBarRand.Value);
}, CancellationToken.None, TaskCreationOptions.None, uicontext);
return (cancel) ? 0 : 1;
}A return value of 0 means the user has asked to cancel the operation. This return code propagates back down the application layers into the enclave. The enclave code looks at the return value of the OCALL to determine whether or not to cancel:
// Make our callback. Be polite and only do this every MB.
// (Assuming 1 KB = 1024 bytes, 1MB = 1024 KB)
if (!(i % 1024)) {
status = o_genrand_progress(&rv, callback, sz, i + 1, kb);
// rv == 0 means we got a cancellation request
if (status != SGX_SUCCESS || rv == 0) return i;
} Enclave Configuration
The default configuration for an enclave is to allow a single thread. As the sample application can run up to three threads in the enclave at one time—the CPUID function on the UI thread and the two RDRAND operations in background threads—the enclave configuration needed to be changed. This is done by setting the TCSNum parameter to 3 in Enclave.config.xml. If this parameter is left at its default of 1 only one thread can enter the enclave at a time, and simultaneous ECALLs will fail with the error code SGX_ERROR_OUT_OF_TCS.
<EnclaveConfiguration>
<ProdID>0</ProdID>
<ISVSVN>0</ISVSVN>
<StackMaxSize>0x40000</StackMaxSize>
<HeapMaxSize>0x100000</HeapMaxSize>
<TCSNum>3</TCSNum>
<TCSPolicy>1</TCSPolicy>
<DisableDebug>0</DisableDebug>
<MiscSelect>0</MiscSelect>
<MiscMask>0xFFFFFFFF</MiscMask>
</EnclaveConfiguration>Summary
Mixing Intel SGX with managed code is not difficult, but it can involve a number of intermediate steps. The sample C# application presented in this article represents one of the more complicated cases: multiple DLLs, multiple threads originating from .NET, locking in native space, OCALLS, and UI updates based on enclave operations. It is intended to demonstrate the flexibility that application developers really have when working with Intel SGX, in spite of their restrictions.