To collect data on a remote Linux* system, a password-less SSH connection is required.
NOTE: A root connection is required to load the sampling drivers and to collect certain performance metrics. You (or your administrator) can configure the system using root permissions and then set up password-less SSH access for a non-root user if desired. For example, build and load the sampling drivers on the target system using root access and then connect to the system and run analysis as a non-root user. If you set up access without using the sampling drivers, then driver-less event-based sampling collection can still be used.
Use one of the methods below to enable password-less SSH access:
- Connection from macOS*/Linux* to Linux
- Connection using PuTTY* from Windows* to Linux
- Connection using Cygwin* from Windows to Linux
NOTE: Instructions below are applicable to VTune Amplifier versions up to 2019 Update 5. For SSH configuration updates introduced with ver. 2019 Update 5, see VTune Amplifier User's Guide.
Enable a password-less connection from macOS/Linux to Linux
For remote collection on a Linux target system, set up the password-less mode on the local Linux or macOS host as follows:
- Generate the key with an empty passphrase:
host> ssh-keygen -t rsa
- Copy the key to target system:
host> ssh-copy-id user@target
Alternatively, if you do not have ssh-copy-id on your host system, use the following command:host> cat .ssh/id_rsa.pub | ssh user@target 'cat >> .ssh/authorized_keys'
- Verify that a password is not required anymore, for example:
host> ssh user@target ls
Configure a Password-less SSH Access with PuTTY from Windows to Linux
For remote collection with PuTTY* Plink from a Windows system, set up the password-less mode as follows:
- Add the path to the PuTTy tools directory to the System variables > PATH variable.
- Launch the PuTTY Key Generator using the puttygen.exe file.
- Click the Generate button (with all default settings intact) to generate keys.
- Click the Save private key button to save the private key to your local drive, for example: C:\Users\user1\private_key.ppk.
- Copy the public key from the PuTTY Key Generator window and paste it to the authorized_keys file on the target Linux system. The authorized_keys file is typically found in the .ssh directory for the target user. For the root user, this would be in /root/.ssh. For other users, it would be in the /home directory.
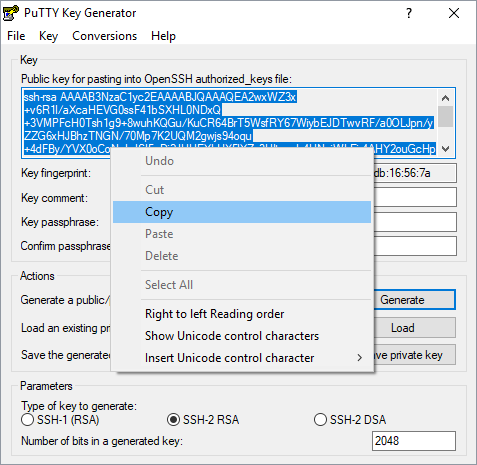
If the file is absent, create it and set the following permissions:chmod 0700 .ssh chmod 0644 .ssh/authorized_keys
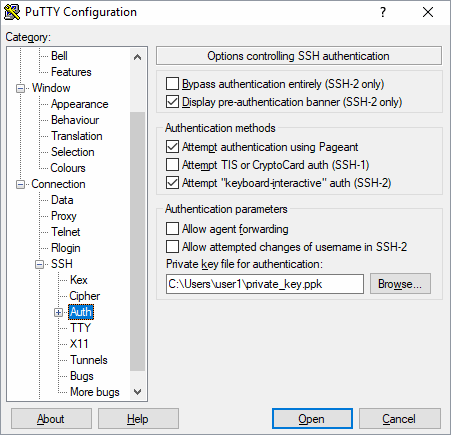
- In the PuTTY Configuration window under the Connection > SSH > Auth category, make sure to have the following settings:
- Under the Session category in PuTTY, click Save to save the private key settings for the Default Settings session and apply them to all subsequent sessions.
NOTE: If you already have PuTTY sessions created before generating the private and public key pair, the keys will not be applied to them. So, you have to either remove the previous sessions in PuTTY, disregard them for VTune Amplifier analysis, or specify a private key for such an existing session.
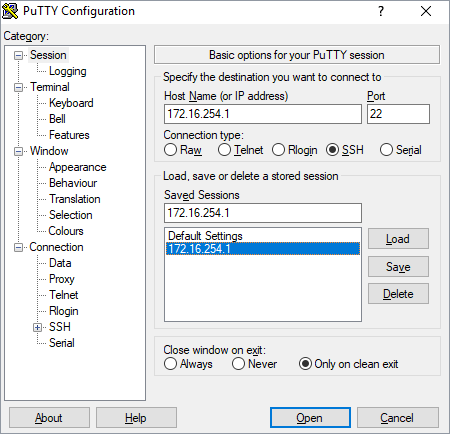
- Create and save a new PuTTY session under the target name. This session name should be used for the VTune Amplifier connection.
For example, you save the session as 172.16.254.1.
Then, when specifying the SSH connection for your remote Linux target, use the same name as a hostname:
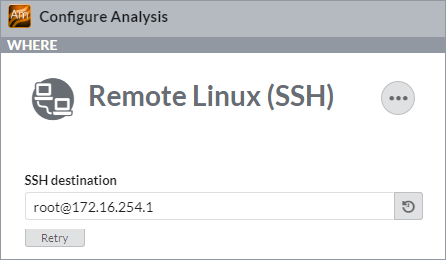
- Verify the connection and make sure the password is not required:
host> plink.exe user@target ls
Configure a Password-less SSH Access with Cygwin* from Windows to Linux
For remote Linux collection with Cygwin from a Windows system, set up the password-less mode as follows:
- Set the CYGWIN_ROOT environment variable as follows:
host> export CYGWIN_ROOT=/cygdrive/c/cygwin64
- Set a path to the Cygwin bin directory:
host> export $PATH=$CYGWIN_ROOT/bin:$PATH
- Create a user directory in CYGWIN_ROOT/home if it does not exist:
host> mkdir $CYGWIN_ROOT/home/hostuser
- Generate the dsa key with an empty passphrase:
host> ssh-keygen -t dsa
- Set correct permissions on the generated file:
host> chmod 600 /home/hostuser/.ssh/id_dsa
- Make sure the .ssh directory exists in the home directory on your device/card. If it is missing, create it.
host> ssh user@target mkdir -p .ssh
- Copy the generated id_dsa.pub file to the device/card:
host> scp /home/user/.ssh/id_dsa.pub user@target:.ssh/authorized_keys
In the command console, you can login to a remote target system without a password. VTune Amplifier GUI will try to find the ssh from environment. You may need to add CYGWIN_ROOT\bin into Windows PATH environment variable so that VTune Amplifier GUI can find the ssh command when doing the remote collection.