The decision to shift computing from on-premise equipment to cloud service providers requires weighing trade-offs. Moving to the cloud allows for efficient scaling and managing of increased computing demand. However, extra steps must be taken to maintain security and privacy previously provided through physical ownership of a dedicated computing environment, now in a cloud environment.
Containers are a great solution for application portability, and provide a degree of isolation between applications, but they bring their own risks. Each container on a system needs access to the kernel, and they share this same kernel with the host OS, providing hackers with a potential channel to attack from container to container, or by just assuming control over the host OS. Similarly, your friendly cloud administrator has a lot of control of your environment. Can you guarantee that they don’t also have visibility into the containers and your proprietary data?
But what if that hacker or sys admin couldn’t see any of your data, even after compromising the system?
Edgeless Systems* and Intel have combined forces to leverage the Intel® Trusted Domain Extensions (TDX) capabilities, on select 4th Gen Intel® Xeon® Scalable instances, to shield your entire Kubernetes* cluster from the underlying cloud infrastructure.
In this demo, Dr Benny Fuhry, Confidential Computing Solution Architect, Intel, and Moritz Eckert, Chief Architect at Edgeless Systems, show how open source project Constellation* encrypts data within the cluster, including runtime in-memory data, and the novel remote attestation capabilities of TDX that enables Kubernetes Node attestation to make the entire cluster verifiable.
Confidential Computing to the Rescue
It’s a standard concept that data should be encrypted when it's being stored (referred to as ‘data protection at rest’.) Similarly, data should be encrypted when it's sent across the network (called ‘data protection in flight’.) This is why transport layer security (TLS) is used to protect communications from eavesdroppers, for example. But what about when data is being processed? Even if the data is encrypted on disk or in the network, it must be decrypted before use. As a result, in a non-confidential computing environment, the plaintext data is accessible in domain memory during processing.
Confidential Computing is a new frontier for data protection. It addresses various security issues by bringing data protection into use through encryption and attestation. The data is encrypted in the main memory, stays encrypted on the data bus, and only gets decrypted inside the CPU. Access controls in the CPU ensure that only specific applications or virtual machines that the data belongs to can access it. Additionally, with attestation, an application or virtual machine can prove mathematically to an external party that its code and data are as expected, that it is protected by specific Confidential Computing hardware, and that this hardware is running with the latest security updates.
Confidential Computing can easily be combined with protection at rest, and protection in flight. With this combination, end-to-end security for the processing and storage of sensitive data can be achieved.
Enhancing Security with Extensions
Years ago, Intel launched Intel® Software Guard Extensions (Intel SGX) to draw a protection perimeter tightly around just the application. Recently, the company introduced additional technology called Intel® Trust Domain Extensions (Intel® TDX) that draws the protection perimeter around virtual machines. As a result, it gets much easier to bring protection in use and attestation to existing workloads.
In this context, a virtual machine is protected by Intel TDX is called the Trust Domain (TD). Such a TD can contain a full operating system or just a minimal kernel, or one application or multiple applications.
Intel TDX's trust boundary around just an individual TD has several consequences. No software outside the TD has access to the code and data inside the TD. This includes the host operating system, hypervisor, and firmware or BIOS. Additionally, a TD is also protected from all other TDs that run on the same server. Furthermore, not even the sys admin managing the TD can gain access.
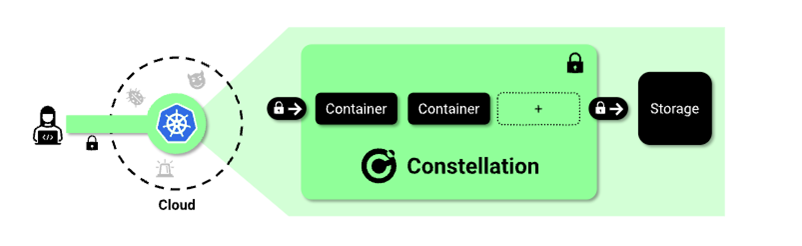
Image: Via Edgeless Systems
Constellation: An Open Source Solution
Edgeless Systems has built an implementation of Intel TDX that brings Confidential Computing to Kubernetes clusters, with an open source product called Constellation. These clusters are completely isolated from the outside, but CNCF*-certified Kubernetes from the inside. This means there’s no need to modify devops procedures related to deploying, managing, or scaling Kubernetes clusters.
Simply encrypting the nodes and containers isn't sufficient security. It's also necessary to protect and verify the control plane, network, and storage, while ensuring they can integrate with current Kubernetes tools and workflows. In the video, Eckert demonstrates how an attestation report that gives details of the state and identity of a confidential virtual machine, can be obtained from TDX. This can be measured against values created by the boot chain and root hash of the file system to ensure that the application being run is the same as its source code, and that it’s running in the expected compute environment.
Try it Out
Edgeless Systems is leading the way with the implementation of Intel TDX capabilities in Constellation to shield an entire Kubernetes cluster from the underlying cloud infrastructure. Data at rest and in transit inside the cluster is encrypted, including at runtime in memory. In addition, the novel remote attestation capabilities of TDX to enable Kubernetes Node attestation, make the entire cluster verifiable.
Check out the video, try it for yourself or book a demo. Constellation is an open source project available on GitHub* so you can see how TDX is implemented in a real-world product. We have a whitepaper with more technical details on how Constellation uses TDX, and you can also read the Constellation documentation and join the Discord channel to chat about confidential computing and Constellation.
Intel TDX will be available on select 4th Gen Intel® Xeon® Scalable instances through leading cloud providers. Select providers are offering previews, check with yours for availability. This demo was first launched at KubeCon + CloudNativeCon Europe 2023.
