Firmware security testing has improved over the past few years but is typically run during platform integration testing, when issues are harder to detect and more expensive to mitigate. Intel is introducing a new analysis framework for firmware development at RSA 2019, allowing developers to unit test firmware components in an OS environment using best-in-class software methods.
Users typically see platform firmware as a single ROM or BIN file. On most systems, it’s a mix of drivers based on the Unified Extensible Firmware Interface (UEFI) or UEFI Platform Initialization (PI) specifications. Because firmware is a low-level part of a computer platform, it has potential security risks that may not be apparent to developers. Validation is critical to delivering robust products with strong root-of-trust.
The most common method of firmware validation is traditional integration testing: code, combine, build, flash, boot, test. It’s possible to check for vulnerabilities in this phase, but the main goal of integration testing is validating platform functionality and stability. These methods are more efficient thanks to automation but don’t isolate errors in specific components. Unit testing is key to isolating issues in components prior to integration, but methods available to driver and application developers have traditionally been difficult to use on firmware components.
Test suites like CHIPSEC and the Intel® Intelligent Test System check platform firmware and hardware configuration at runtime. These tests are focused on artifacts firmware leaves behind, such as register configuration and runtime interfaces… what the firmware *did* instead of how the firmware did it. Projects like Excite use symbolic execution, fuzzing, and testing to find vulnerabilities in sensitive code, but as part of firmware on a Wind River* Simics* virtual platform.
These tests provide improvements in overall firmware security, but they are designed to operate on integrated firmware images. These issues are more expensive to mitigate than those found during design or implementation. Developers need a robust toolset for analyzing firmware components prior to unit testing or integration testing.
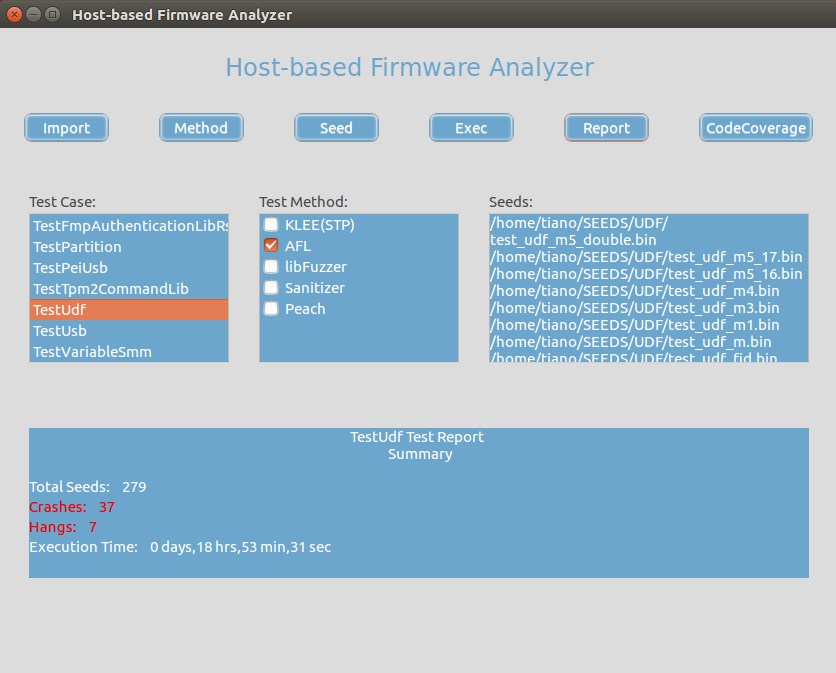 To help reduce issues prior to integration, Intel has developed a new open source tool: Host-based Firmware Analyzer (HBFA). This environment enables advanced testing of UEFI and UEFI PI drivers in the developer’s OS environment. The test suite utilizes existing open source tools to tests with common fuzzing frameworks, symbolic execution, address sanitization, code coverage reports, and methods for fault injection and trace. These test methods have rarely been applied to firmware components since unlike drivers and applications they lack direct interfaces to the OS. It is possible to create this sort of test environment in firmware, but it lacks the speed and flexibility of a full OS environment for execution.
To help reduce issues prior to integration, Intel has developed a new open source tool: Host-based Firmware Analyzer (HBFA). This environment enables advanced testing of UEFI and UEFI PI drivers in the developer’s OS environment. The test suite utilizes existing open source tools to tests with common fuzzing frameworks, symbolic execution, address sanitization, code coverage reports, and methods for fault injection and trace. These test methods have rarely been applied to firmware components since unlike drivers and applications they lack direct interfaces to the OS. It is possible to create this sort of test environment in firmware, but it lacks the speed and flexibility of a full OS environment for execution.
HBFA introduces a stub interface for firmware components based on TianoCore EDK II. This innovative method applies best-in-class software practices to platform firmware development, incorporating high-level software testing that detects commonly exploitable issues in drivers, libraries, and programs prior to deployment. HBFA extends an interface for tools like AFL, Peach, and KLEE to execute test cases on firmware components prior to system integration.
In April 2019, Intel contributed HBFA to the TianoCore open source community. This is in addition to existing guidelines for secure code design, code review, test strategies, and test tool development. For more information, please refer to the ‘Using Host-based Firmware Analysis to Improve Platform Resiliency’ whitepaper or check out HBFA in github.