Terminology
| Term | Definition |
|---|---|
|
CoRIM |
Concise Reference Integrity Manifest |
|
Intel® SGX / Intel® TDX DCAP |
Intel® Software Guard Extensions Data Center Attestation Primitives / Intel® Trust Domain Extensions for Data Center Attestation Primitives
|
| Intel® Provisioning Certification Services (Intel® PCS) |
Intel® Provisioning Certification Services (Intel® PCS) provides a set of APIs for retrieving provisioning certificates, revocation lists, and trusted computing base (TCB) information for confidential computing. |
|
Intel® SGX |
Intel® Software Guard Extensions |
|
Intel® TDX |
Intel® Trust Domain Extensions |
|
Platform Composition Manifest |
An Intel-signed document which attests that a processor—identified by its Processor Registration ID (PRID)—is contained within the Platform Instance Identity (PIID)-identified platform. |
|
Platform Endorser |
A service that takes in a Platform Manifest or platform ID (PIID) and provides a Platform Ownership Endorsement (POE). |
|
Platform Identifier |
Unique identifier to the platform instance. |
|
Platform Instance Identity (PIID) |
Unique identifier to the platform instance that is generated on first boot of the platform; a new identifier can be regenerated after being manually triggered by an Intel SGX factory reset. |
|
Platform Manifest |
The Platform Manifest allows the registration authority service to evaluate whether the platform and its component processor packages are suitable for being certified as an Intel SGX or Intel TDX platform. The Platform Manifest contains the Platform Instance Identity (PIID) and each processor’s PRID. It’s generated on the platform’s first boot, some Trusted Computing Base Recoveries (TCB-R), and after a manually triggered Intel SGX factory reset. |
|
Platform Owner |
Trusted authority that manages and secures platforms in a given deployment context. |
|
Platform Ownership Endorsement (POE) |
An endorsement created by the owner of a platform to claim ownership of a platform. |
|
Processor Registration ID (PRID) |
Unique identifier to an individual processor that remains constant for its entire lifetime. |
|
Quote Verification Library |
A software library to verify the authenticity and integrity of an attestation quote generated by Intel SGX or Intel TDX |
|
Trusted Supply Chain Inventory |
In the more advanced architecture, the central entity responsible for secure collection of processors identifiers (such as PRIDs) during the controlled supply chain phase of deployment. The Trusted Supply Chain Inventory makes its secure list of PRIDs available to POE Endorsers. |
Introduction
Physical security is an important consideration when developing a comprehensive, multi-layered security strategy, including virtual machine and application protections enabled through confidential computing. No platform can be absolutely secure from physical attacks. However, a Platform Ownership Endorsement (POE) enables remote parties to establish who is in possession of the platform, providing physical security to reduce the risk of physical attacks on the platform.
This technical paper discusses the POE architecture and tools that Intel is developing to simplify POE deployment and aid in the interoperability of customer solutions and other Intel infrastructure. Intel has plans to incorporate POE in a future Intel® Software Guard Extensions Data Center Attestation Primitives / Intel® Trust Domain Extensions Data Center Attestation Primitives (Intel® SGX DCAP / Intel® TDX DCAP) release to enable customers using the Intel SGX DCAP / Intel TDX DCAP Quote Verification library.
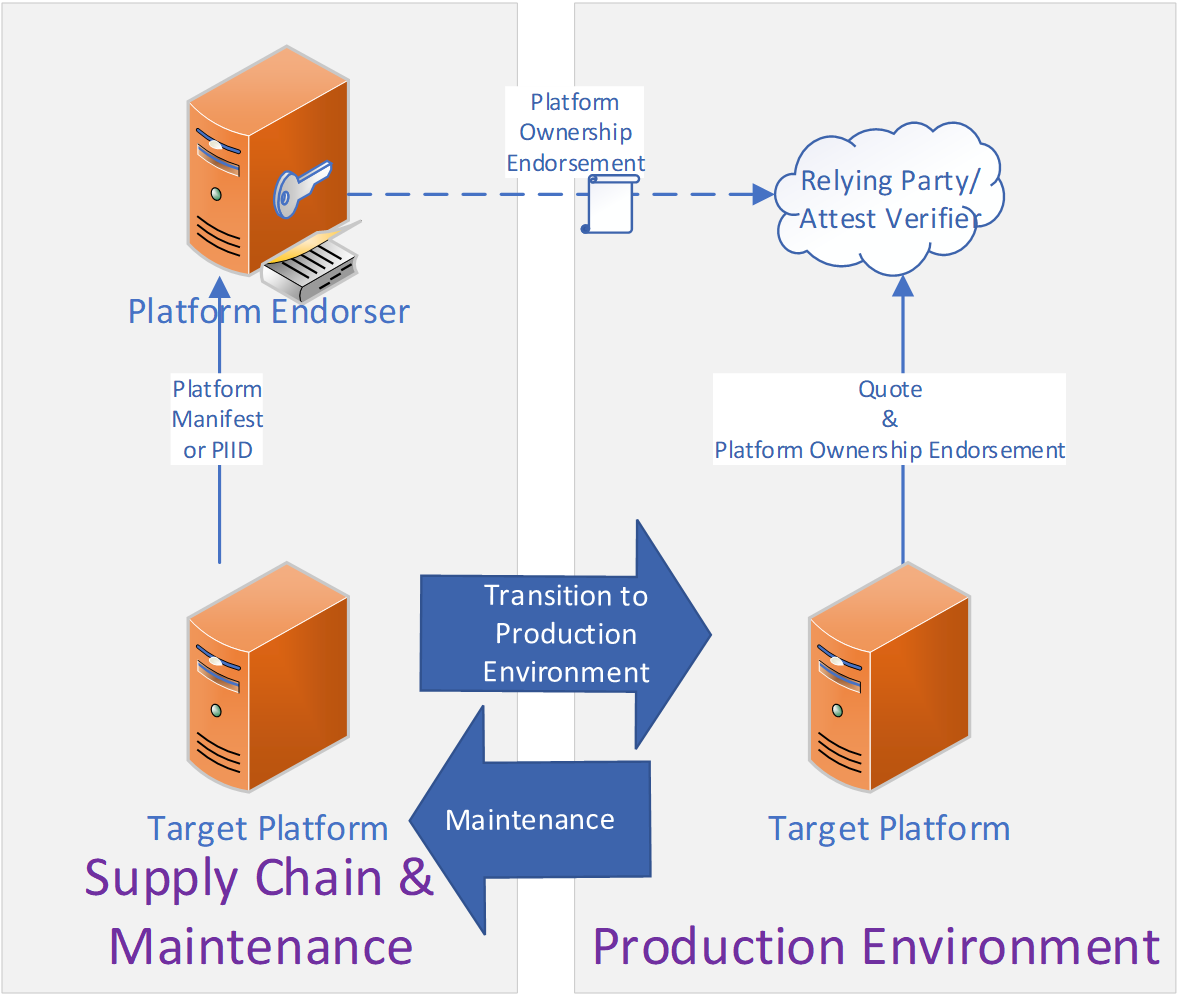
Figure 1: Platform Ownership Endorsement Flow Overview depicts a high-level view of creating and using a POE. During the supply chain deployment or maintenance, the Platform Endorser collects platform attestation identities from their platforms and issues POEs for each platform’s identity. This endorsement can be returned to the platform to be included with attestations, or take a different path, to the Attestation Verifier. In the production environment, during attestation, the Attestation Verifier also verifies the POE to confirm the identity of the Platform Owner. The verifier can then approve attestations that both meet the attestation policy and have a verified owner trusted to provide physical protection to the platform, rounding out the multilayered security model.
The Platform Ownership Endorsement for Intel® Software Guard Extensions (Intel® SGX) and Intel® Trust Domain Extensions (Intel® TDX) section describes the critical architecture components and tools to simplify each stage of the process. The POE Creation with Platform Composition Endorsements section describes an added security step in the Supply Chain and Maintenance flows to limit trust in the maintenance administrator.
Platform Ownership Endorsement for Intel® Software Guard Extensions (Intel® SGX) and Intel® Trust Domain Extensions (Intel® TDX)
The ownership endorsement process starts when the owner collects unique platform identifiers from each platform in their possession, and then creates an endorsement (POE) for each of those platforms.
The platform identifier is the critical component of the POE and must be a globally unique value also found in every attestation. The ideal identifier is one that has many supply chain points where it can be collected and endorsed and can easily be reset if the platform changes ownership, effectively invalidating the prior endorsement before the platform changes hands.
The platform identifier common to Intel SGX and Intel TDX attestation on Intel® Xeon® processors (excluding Intel® Xeon® E processors) with these properties is called the Platform Instance Identity (PIID). The PIID is generated during the first boot of the platform, is regenerated after manually triggered Intel SGX factory resets1, but remains constant across other platform lifecycle events, such as Trusted Computing Base Recoveries. The PIID can be found in the attestation related structures: the Platform Manifest created during first platform boot flow for Platform Registration and in the Provisioning Certification Key (PCK) certificate that’s part of every attestation.
A complete POE solution includes four ingredients annotated in Figure 2: Platform Ownership Endorsement Components:
- A collection of platform identifiers of all platforms during supply chain deployment or maintenance.
- Generation and signing of the POE.
- Distribution of POE.
- Verification of the POE during attestation.
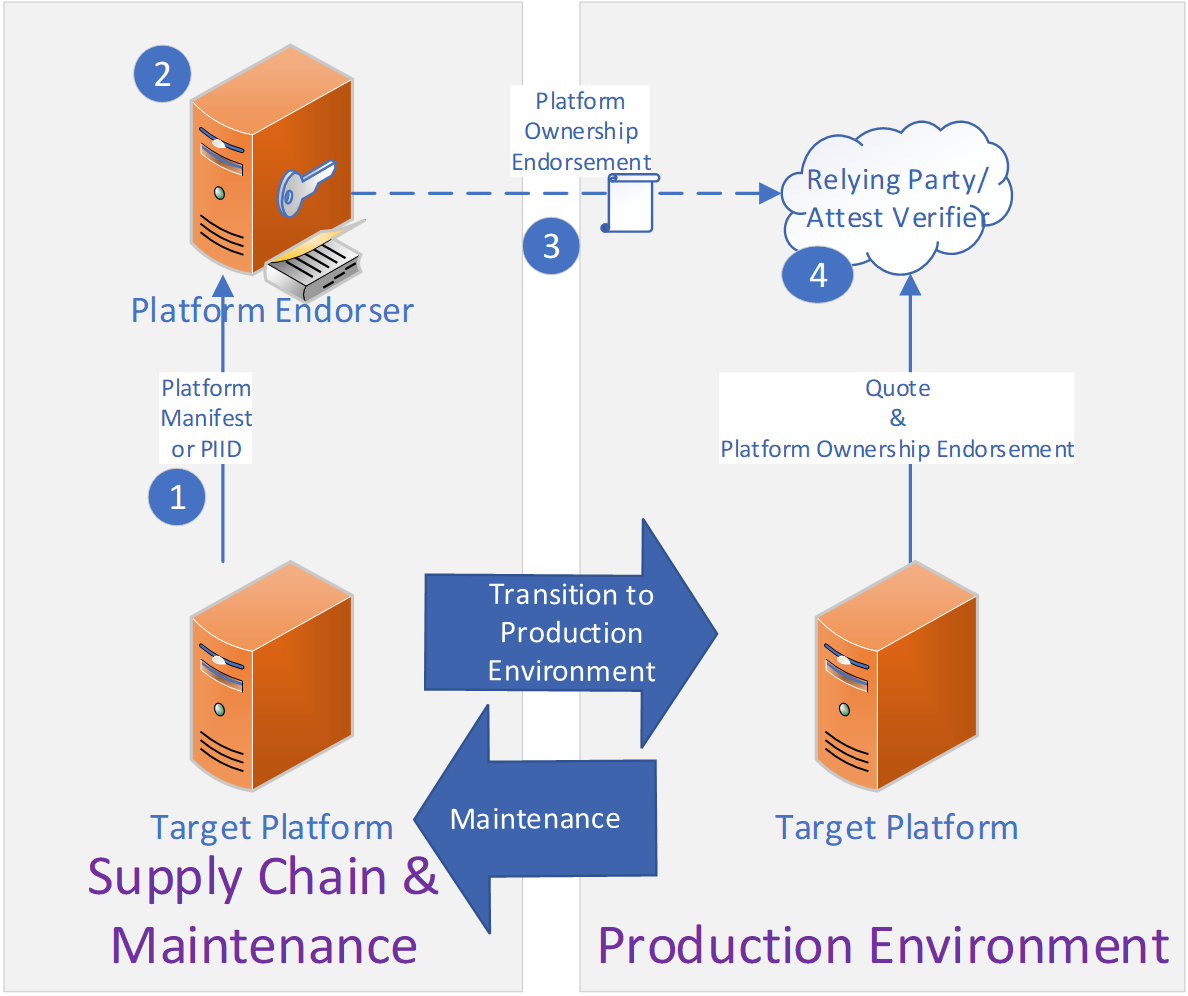
The next sections describe the best-known methods for each of these components for Intel SGX and Intel TDX. The details in these descriptions are examples; more sophisticated deployment scenarios such as co-location etc. may split, merge, or delegate these responsibilities differently than depicted here.
Platform ID Collection
To endorse platforms the owner is in possession of, the owner must identify each platform in their possession and keep track of these platforms. To achieve that, the platform owner should first retrieve a structure that contains the PIID, for example, the Platform Manifest or a PCK Certificate, from each platform. Second, the platform owner (Figure 2, step 1) stores these structures in a database or (Figure 2, step 2) extracts the PIIDs from the structures and stores them in a database. The resulting database is provided to the Platform Endorser or as transactions sent to the Platform Endorser.
Details regarding when and how PIIDs (or any structure containing PIIDs) are collected depend on many factors of the environment, such as the process of the supply chain, on-boarding, platform configuration, burn in, platform testing, and final deployment. However, the collection and storage should be done in a secure, controlled environment at some point between platform acquisition and final deployment.
The PIID of a platform should be recollected whenever a new PIID is generated, which occurs on the first boot of a platform and any manually triggered Intel SGX factory reset. Refer to the “SGX Multi-Package States” section in the Remote Attestation for Multipackage Platforms Using Intel® SGX Datacenter Attestation Primitives guide for a more complete list of types of maintenance events and their impact on PIID.
The POE Creation with Platform Composition Endorsements section describes ways to remove the need to re-establish a secure environment where administrators performing maintenance can recollect PIIDs during some maintenance events.
Endorsing Platforms
The exact construction of the Platform Endorser is environment-specific. It should ensure that the Platform Endorser only creates endorsements for identities of platforms whose possession was confirmed in the process in the Platform ID Collection section.
The POE itself can take many forms; the only requirement is that it is signed by the platform owner and includes the platform’s PIID. However, by selecting a preferred format, different implementations of Platform Endorsers, Attestation Verifier Services, and Service Trust Domains (Service TDs) can share the same logic for processing these endorsements. Intel recommends using IETF CoRIM because it is a standardized format that Intel plans to increasingly adopt over time for attestation endorsements and reference values.
The planned Intel® Platform Ownership Endorsement Generator (Intel® POE Generator) tool will assist an endorser by extracting the PIID from collected Platform Manifests or PCK Certificates and generating a POE in an unsigned CoRIM. The Platform Endorser can then sign the POE, and the associated public key represents that platform owner. After the POE is signed, the Intel® POE Generator can insert the signature to the correct location within the POE.
Ownership Endorsements Distribution
To be effective, the platform owner must make the POEs available to potential Attestation Verifier services. In the future, Intel will add this POE into the existing Intel SGX DCAP / Intel TDX DCAP attestation stack, similar to the way it adds other endorsements to the Quote.
Until then, platform owners will need to distribute POEs to ensure intended Attestation Verifiers can access these endorsements. Some owners may choose to store these endorsements centrally indexed by their PIID.
In POE deployments with a centrally stored POE database, the Intel® Platform Instance ID Extractor (Intel® PIID Extractor) tool will aid in selecting the correct POE by extracting the PIID from the Quote being verified. An alternative POE deployment may choose to have platform software concatenate the POE to the end of Quotes, allowing them to be communicated through existing attestation protocols.
Endorsement Verification
The Attestation Verifier will need to include a POE verification in their attestation processing steps. This check should confirm that the POE is present, has a PIID that matches the Quote, and was signed by a key belonging to the expected platform owner. If these all pass approval, the verifier knows this attestation came from a platform owned by the expected owner.
The planned Intel® Platform Ownership Endorsement Evaluator (Intel® POE Evaluator) tool/library will aid the Attestation Verifier in processing these endorsements. It will accept a Quote and a POE created by the Intel POE Generator tool, verify the integrity of the POE, and return the certificate chain of the Platform Endorser. The Attestation Verifier only needs to confirm that this chain represents an approved party.
POE Revocation
Intel recommends conducting an Intel SGX / Intel TDX Factory Reset before a platform changes possession. This will wipe all Intel SGX / Intel TDX keys as well as reset the platform’s PIID, which is the link between the platform’s attestation and the POE. While this does not technically revoke the POE, the POE will not match any attestations created by the platform after the factory reset, effectively nullifying the old POE.
POE tokens issued by Intel tools will include a validity period after which they expire and need to be reissued. Optionally, by shortening the validity period, a platform owner can cause the POE to expire for platforms it no longer owns.
POE Creation with Platform Composition Endorsements
During maintenance events, such as a factory reset or processor replacement, a new PIID is generated. In some environments, it is desirable to introduce an additional layer of security before creating POEs for PIIDs generated during such events, particularly when administrator trust is limited. In these cases, the Platform Endorser desires further evidence to ensure that the new PIID represents a platform composed exclusively of devices owned by the endorser. This is achieved by a Trusted Supply Chain Inventory Tracker service that is solely trusted with identifying and inventorying devices during the more-controlled supply chain. Regular endorsements that may occur multiple times in the platform’s lifecycle rely on this inventory rather than interactions with the platform in less-controlled maintenance environments.
To enable this additional layer of security, processor registration IDs (PRIDs) must be collected. The PRID of each processor is contained within the Platform Manifest.
A new Intel® Provisioning Certification Services (Intel® PCS) interface will take a Platform Manifest as input and provide an Intel-signed Platform Composition Manifest, which endorses that a PIID belongs to a platform composed of specific PRID(s). The Platform Composition Manifest is independently verifiable, which supports offline auditing. In contrast, the Platform Manifest is only verifiable by Intel.
Figure 3: POE Creation with Platform Composition Manifest shows an example of how this architecture can be designed with these primitives.
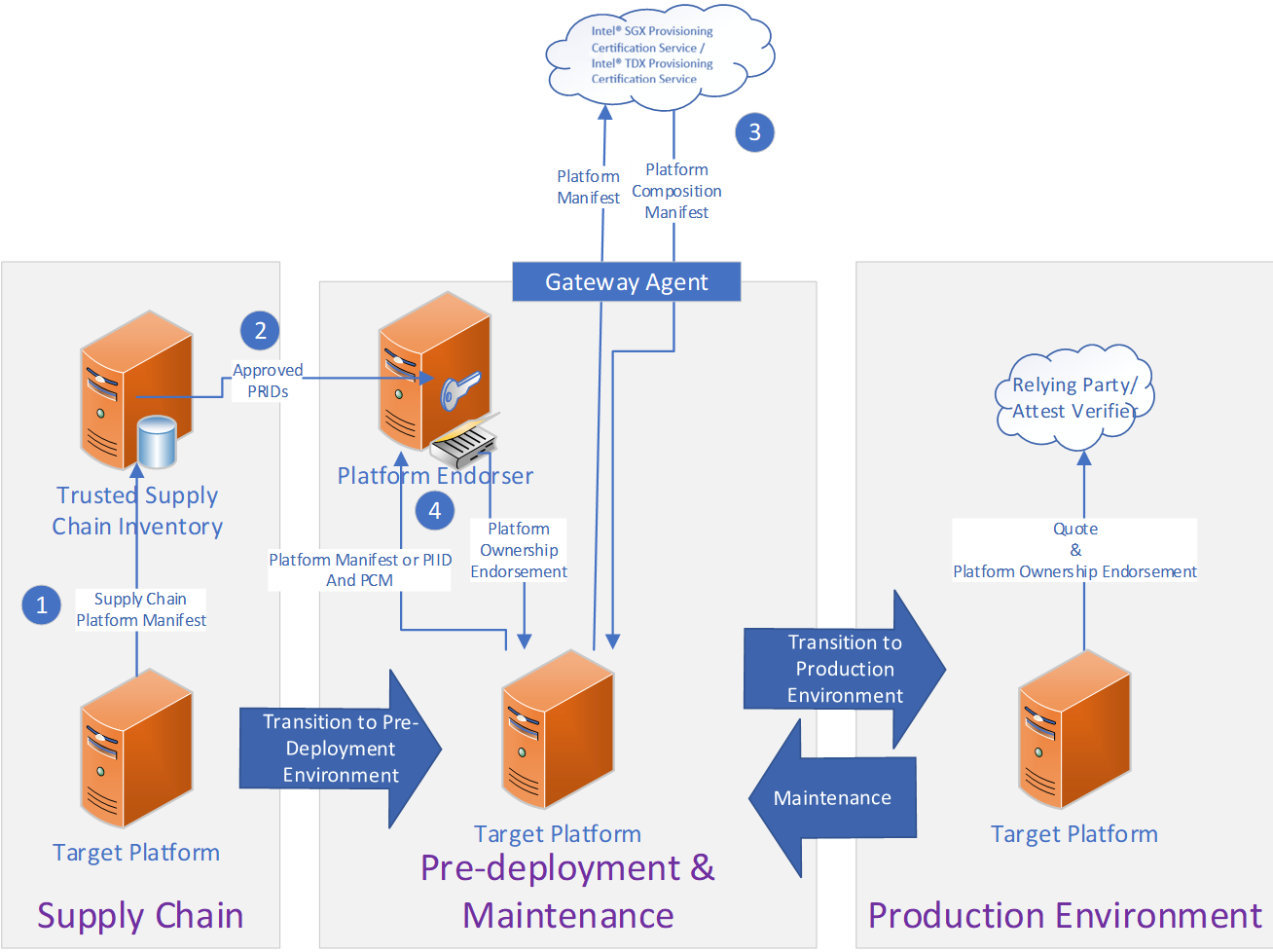
During the datacenter’s supply chain phase, the Trusted Supply Chain Inventory service collects Supply Chain Platform Manifests (Figure 3, step 1) from every platform during the datacenter’s supply chain process. The platform manifest contains the PRIDs of every processor, which can be extracted using the Intel® Processor Registration ID Extractor (Intel® PRID Extractor) tool that Intel plans to release. The inventory service assembles an authenticated list of Approved PRIDs that are owned by the Inventory owner. This list is communicated to the Platform Endorser (Figure 3, step 2). After manifest collection, the platform transitions into pre-deployment phase.
When a platform generates a new PIID, in either pre-deployment or maintenance, an agent sends the new Platform Manifest to the Intel® Provisioning Certification Services (Intel® PCS) (Figure 3, step 3) and receives a signed Platform Composition Manifest (PCM).
The flow continues as described in the Introduction section, except that the Request for certification (Figure 3, step 4) contains a Platform Composition Manifest in addition to a Platform Manifest or PIID. A POE is only issued by Platform Endorser for PIIDs accompanied by an Intel-signed Platform Composition Manifest that contains only PRIDs on the Trusted Supply Chain Inventory system’s Approved PRID list.
In this architecture, a compromised maintenance administrator cannot endorse a PIID for a platform not owned by the platform owner. Only PIIDs composed of processors certified by the Trusted Supply Chain Inventory service will be endorsable. This allows the Trusted Supply Chain Inventory service to be an offline or otherwise hardened service with fewer administrators than the rest of the fleet.
Summary
Although no platform can be completely secure from physical attacks, Intel’s POE architecture allows remote parties to identify who provides physical protection to a platform before trusting an attestation created by that platform. The tools described in this paper will simplify the deployment of POE processing with a long-term plan to integrate these tools seamlessly into the existing Intel SGX DCAP / Intel TDX DCAP software stack. The tools Intel is developing are:
- Intel® Platform Instance ID Extractor (Intel® PIID Extractor) to extract PIIDs from TEE Attestations.
- Intel® Processor Registration ID Extractor (Intel® PRID Extractor) to extract PRIDs from Platform Manifests.
- Intel® Platform Ownership Endorsement Generator (Intel® POE Generator) to generate Platform Ownership Endorsements.
- Intel® Platform Ownership Endorsement Evaluator (Intel® POE Evaluator) to evaluate Platform Ownership Endorsements.
These tools will be released in the near future. Intel recommends following Intel’s POE architecture to incorporate these tools into your solution, including using the CoRIM format to promote interoperability and security.
Resources
- Intel® TDX DCAP Quoting Generation Library and Quote Verification Library
- Supporting Intel® SGX on Multi-Package Platforms
- Remote Attestation for Multipackage Platforms Using Intel® SGX Datacenter Attestation Primitives
- Intel® SGX PCK Certificate and Certificate Revocation List Profile Specification
- Concise Reference Integrity Manifest
 Footnotes
Footnotes
- An Intel SGX factory reset can be done at any point in time and is highly recommended before waterfalling a platform.