
The Android* Keystore system lets you store cryptographic keys in a container to make them more difficult to extract from the device. Once keys are in the keystore, you can use them for cryptographic operations, with the key material remaining non-exportable. Also, the keystore system lets you restrict when and how keys can be used, such as requiring user authentication for key use or restricting keys to use only in certain cryptographic modes. — Android Developer Website.
This article describes our collaboration with TongxinMicro to design and implement StrongBox KeyMint functionality on the Celadon code base, where we combined Intel’s integration capabilities with TongxinMicro’s robust security IC and COS solutions. We have completed enabling the StrongBox Proof of Concept on Celadon (Android 13). This validation encompassed the communication between StrongBox and Trusty KeyMint, ensuring seamless integration and interoperability. Additionally, the associated Vendor Test Suite (VTS) and Compatibility Test Suite (CTS) tests have yielded exceptional results, with nearly 100% of the tests passing successfully.
What is StrongBox KeyMint?
Key material can be bound to the secure hardware of the Android device, such as the Trusted Execution Environment (TEE) or Secure Element (SE). When TEE or SE is enabled for a key, its key material is never exposed outside of secure hardware. If the Android OS is compromised or an attacker can read the device's internal storage, the attacker might be able to use any app's Android Keystore keys on the Android device, but it can't extract them from the device. This feature is enabled only if the device's secure hardware supports the combination of key algorithms, block modes, padding schemes, and digests for which the key is authorized.
The diagram below shows the architecture of the StrongBox KeyMint Keystore:
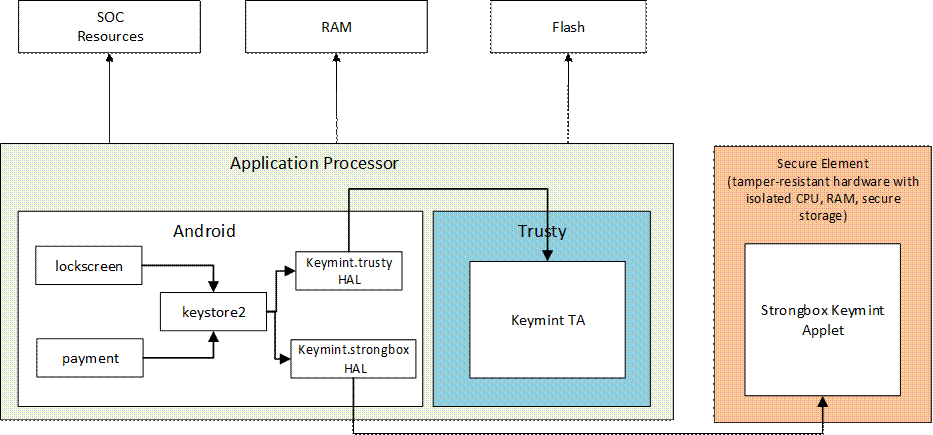
StrongBox KeyMint: An additional keystore type
In contrast to TEE, which runs its own OS and communicates with the Android OS only through a restricted interface, StrongBox KeyMint goes one step further; it has a separate microchip with its own CPU, storage, RAM, etc. It is designed specifically for security-relevant purposes, such as tamper-resistant protection in emerging user features aiming to secure sensitive data and to enable secure communication. The module contains the following:
- A CPU
- Secure storage
- A true random-number generator
- Additional mechanisms to resist package tampering and unauthorized sideloading of apps
- A secure timer
- A reboot notification pin (or equivalent), like a general-purpose input/output (GPIO)
To support low-power StrongBox implementations, a subset of algorithms and key sizes are supported:
- RSA 2048
- AES 128 and 256
- ECDSA, ECDH P-256
- HMAC-SHA256 (supports key sizes between 8 bytes and 64 bytes, inclusive)
- Triple DES
- Extended Length APDUs
- Key Attestation
- Amendment H support for upgrade
When generating or importing keys using the KeyStore class, you indicate a preference for storing the key in the StrongBox KeyMint by passing true to the setIsStrongBoxBacked() method.
Android Ready SE Alliance
StrongBox and tamper-resistant hardware are becoming essential requirements for new user applications, including digital keys (car, home, office), mobile driver’s license (mDL), national ID, ePassports, and eMoney solutions (for example, Wallet*), etc. It is important to note that these features are not just for phones and tablets. StrongBox is also applicable to Wear OS by Google*, Android Auto*, and Android TV*. All these features must run on tamper-resistant hardware to protect the integrity of the application executables and a user’s data, keys, wallet, and more. Most modern phones now include an SE.
To boost the adoption of new Android use cases, Google has established the Android Ready SE Alliance, a collaborative effort with SE vendors to develop open-source, validated SE Java Card Applets and Hardware Abstraction Layer (HALs). Several SE vendors, including Giesecke+Devrient*, Goodix*, Kigen*, NXP*, Samsung*, ST, Thales, TongxinMicro, Unisoc*, and Valid, have joined the alliance.
OEMs that adopt Android Ready SE can produce highly secure devices and allow for remote updates to enable compelling new cases as they become available on the Android platform. Consumers will benefit from their devices being more secure and updatable with new capabilities.
StrongBox in Celadon
Starting with Android 6.0, Celadon has actively supported Trusty Backed Keymaster, an essential component for secure key storage and cryptographic operations. Over the years, Keymaster has iterated through multiple versions, ranging from 0.3 to 4.1 and then to the latest KeyMint 3.0. The development and refinement of Trusty Backed Keymaster has been pivotal in ensuring the security of sensitive information on Android devices. Increasingly, sensitive user cases such as mDL, ePassports, eMoney solutions, etc., must run on tamper-resistant hardware with StrongBox KeyMint support.
According to the Android 13 Compatibility Definition (CDD) requirements provided by Google, StrongBox is currently classified as STRONGLY RECOMMENDED, and it will likely become a MUST requirement in a future release.
While exploring potential hardware solutions for StrongBox KeyMint support, Celadon came across the Android Ready SE Alliance list. We discovered TongxinMicro’s THD89 chip , which fulfilled the necessary requirement of tamper-resistant hardware for enabling StrongBox KeyMint functionality, making it a suitable candidate for collaboration.
Celadon initiated a collaboration with TongxinMicro to explore integrating the THD89 SE chip within the Celadon platform to support StrongBox KeyMint 2.0. Through cooperation and extensive discussions, Celadon and TongxinMicro devised an architecture that effectively incorporates the THD89 chip into the Celadon framework.
Architectural Overview of StrongBox in Celadon
The diagram below illustrates the key components and their interactions, providing an overview of how the THD89 chip facilitates the implementation of StrongBox KeyMint 2.0.
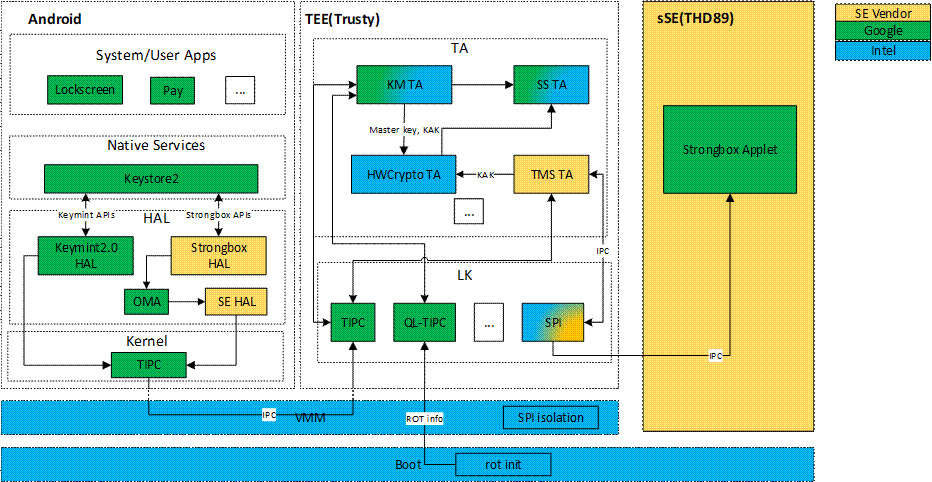
Architecture Overview of StrongBox in Celadon
As the SE vendor, TongxinMicro provides the StrongBox HAL, which implements the APIs related to StrongBox KeyMint. The StrongBox HAL utilizes the Open Mobile API (OMA) to translate incoming requests into TongxinMicro’s stable interface. TongxinMicro provides the SE HAL to access the embedded Secure Element (eSE). It establishes communication with the Trusty Management Service (TMS) TA through the TIPC mechanism. The TMS TA is a new application added to Trusty to handle requests from the SE HAL to the eSE via the SPI driver.
The StrongBox Applet, provided by Google, is an implementation of a Java Card* applet responsible for executing StrongBox KeyMint-related functionalities within the eSE environment.
The Key Agreement Key (KAK) generated by the HWCrypto TA calculates a HMAC key shared between Trusty and Strongbox. The key is used to compute MAC and verify authentication tokens between Trusty and StrongBox to validate the authenticity of messages produced by each other.
During boot, the Trusty KeyMint TA retrieves Root of Trust (ROT) information. Its structure is defined by Android, which gets data such as verify boot state, device lock state, OS version, etc., from the bootloader and sends it to the Strongbox.
This architecture diagram above demonstrates the flow and interaction between the components enabling StrongBox KeyMint functionality. The StrongBox HAL, OMA, SE HAL, TMS TA, StrongBox Applet, and Trusty Kernel work together to facilitate secure communication and execute Strongbox-related operations within the eSE environment.
Conclusion
With the successful validation of StrongBox functionality, we can confidently state that Celadon has put in place the final piece of the puzzle regarding the requirements for Keymaster. This achievement signifies that we can meet the CDD requirements related to StrongBox Keymaster. By fulfilling these requirements, we are better positioned to effectively address our customers' needs.
About the Author
Shaopu Yan is a senior OS software engineer at Intel, with deep experience in computer operating systems, virtualization, trusted execution environment (TEE), and confidential computing.
About TongxinMicro
As the principal enterprise of automotive electronics and smart chips in the Tsinghua Unigroup, whose business area covers smart cards, consumer electronics, automotive electronics, MCU, memory, and devices, we have accumulated industry-leading chip R&D technology and wafer testing capabilities, won the First Prize of National Science and Technology Progress Award, gotten CC EAL6+, GSMA SAS-UP, AEC-Q100 Grade1, ISO 26262 ASIL-D, and other awards and certifications. We have nearly 300 authorized patents and have developed into an industry-leading semiconductor solution provider.
References
https://www.focus-rfid.com/high-performance-security-chip-thd89-series-product/
https://developers.google.com/android/security/android-ready-se
https://developer.android.com/training/articles/keystore
https://www.tsinghuaic.com/index/index/show/id/11
https://github.com/divegeek/JavaCardKeymaster/tree/Javacard_KeyMint_200_master
Notices
Android is a trademark of Google LLC.