Intel® Active Management Technology 9
Download PDF
Intel® Active Management Technology (Intel® AMT) Start Here Guide (Intel AMT 9.0) [PDF 804KB]
Contents
2.1 What is Intel® Active Management Technology?
2.2 What is new with the Intel® AMT Release 9.0
2.3 Preparing your Intel® AMT Client for use
4 Client Control Mode and Admin Control Mode
4.1 Client Control Mode Limitations
4.2 Manually Configuring an Intel AMT 9.0 Client
5 Accessing Intel® AMT via the WebUI Interface
6 Intel® AMT Drivers and Services
6.1 NIC: Intel Ethernet Connection
6.2 Intel® Management Engine Interface
6.3 Serial-Over-LAN (SOL) Driver
6.4 Intel® Active Management Technology LMS Service
6.5 Intel® AMT User Notification Service (Pre Intel AMT 9.0)
6.6 Intel Management and Security Status Tool
7 Intel® AMT Software Development Kit (SDK)
7.1 Other Intel AMT SDK Resources
1 Introduction
This document contains information that aids developers in getting started with implementing Intel® Active Management Technology (Intel® AMT). It provides an overview of the features in various versions of Intel AMT, as well as information on minimum system requirements, configuration of an Intel AMT client, and the various developer tools that are available to help program for Intel AMT.
Intel AMT supports remote applications running on Microsoft Windows* or Linux*. Intel AMT Release 2.0 and higher support only Windows-based local applications. For a complete list of system requirements, please refer to the documentation in the latest Intel® AMT Software Development Kit (SDK).
2 Getting Started
In order to begin managing an AMT client or running samples from the SDK, you will need a separate system to use as a management console for remotely managing your Intel AMT client. For more detailed explanations, please refer to the Intel® AMT Implementation and Reference Guide located in the Docs folder of the Intel AMT SDK.
2.1 What is Intel® Active Management Technology?
Intel AMT is part of the Intel® vPro™ technology[i] offering. Platforms equipped with Intel AMT can be managed remotely, regardless of whether they are powered up or whether they have a functioning OS.
The Intel® Manageability Engine (Intel® ME) is the steam behind Intel Active Management Technology. As a component of the Intel vPro platform, Intel AMT uses a number of elements in the Intel vPro platform architecture. The following figure shows the relationship between these elements.
Notice that there is a network connection directly associated with the Intel ME. The specific NIC will change according to which Intel AMT release you are using.
The Intel AMT functionality is contained in the Intel ME firmware.
- The firmware image is stored in flash memory.
- The Intel AMT capability is enabled using the Intel® Manageability Engine (Intel® ME) BIOS extension as implemented by an OEM platform provider. A remote application can be used to perform enterprise setup and configuration.
- On power-up, the firmware image is copied into the Double Data Rate (DDR) random-access memory (RAM).
- The firmware executes on the Intel® processor with Intel ME and uses a small portion of the DDR RAM (Slot 0) for storage during execution. RAM slot 0 must be populated and powered on for the firmware to run.
- Intel AMT stores the following information in flash (ME Data):
- OEM-configurable parameters
- Setup and configuration parameters such as passwords, network configuration, certificates, and access control lists (ACLs)
- Other configuration information, such as lists of alerts and System Defense policies
- The hardware configuration captured by the BIOS at startup
Details for 2013 platforms with Intel vPro technology (Release 9.x) are as follows:
- 22nm process
- Platform (Mobile and Desktop): 4th generation Intel® Core™ processor (codename Shark Bay)
- CPU: Haswell (code name)
- PCH: Lynx Point (code name)
2.2 What is new with the Intel AMT Release 9.0
- Any configuration software can now synchronize the Intel AMT network time to coordinate with UTC. See the section called “Enable Local Time Sync” in the Intel® AMT Implementation and Reference Guide.
- The Intel AMT network can now be enabled and disabled. See the section called “Enable/Disable Intel AMT Network” in the Intel® AMT Implementation and Reference Guide.
- The User Notification Service and Local Manageability Service capabilities have been unified into a single group of capabilities now referred to collectively as the Local Manageability Service. See the section called “Local Manageability Service” in the Intel® AMT Implementation and Reference Guide.
- The ability to configure a headless platform remotely without the need for local user-consent has been added.
- Intel AMT 9.0 supports 5 new power states in order to support the added Graceful Shutdown feature. See the section called “Change System Power State” in the Intel® AMT Implementation and Reference Guide.The new power states are:
- 4: Sleep-Deep, corresponding to ACPI state G1, S3, or D2
- 7: Hibernate (Off Soft), corresponding to ACPI state S4, where the state of the managed element is preserved and will be recovered upon powering on
- 11: Diagnostic Interrupt (NMI) corresponding to the system reaching ACPI state S5 followed by ACPI state S0. This is used to represent system non-maskable interrupt.
- 12: Off – Soft Graceful, equivalent to Off Soft but preceded by a request to the managed element to perform an orderly shutdown.
- 14: Master Bus Reset Graceful, equivalent to Master Bus Reset but preceded by a request to the managed element to perform an orderly shutdown.
- Intel AMT devices will no longer have the ability to integrate into Cisco NAC systems.
2.3 Preparing your Intel AMT Client for use
The following diagram illustrates the modes or stages that an Intel AMT device passes through before it becomes operational.
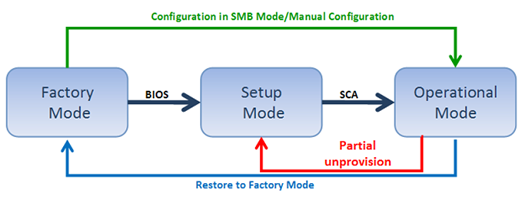
Before an Intel AMT device can receive its configuration setting from the Setup and Configuration Application (SCA), it first must be prepared with initial setup information and placed into Setup Mode. The initial information will be different, depending on the available options in the Intel AMT release, and the settings performed by the platform OEM. The following table summarizes the methods you can use to perform setup and configuration on the different releases of Intel AMT.
| Legacy | 1.0; Releases 2.x and 3.x in legacy mode | Setup and Configuration in Legacy Mode |
| SMB | 2.x, 3.x, 4.x, 5.x | Setup and Configuration in SMB Mode |
| PSK | 2.0 and later | Setup and Configuration Using PSK |
| PKI | 2.2, 2.6, 3.0 and later | Setup and Configuration Using PKI (Remote Configuration) |
| Manual | 6.0 and later | Manual Setup and Configuration (from Release 6.0) |
| CCM, ACM | 7.0 and later |
Note that the Intel® Setup and Configuration Software (Intel® SCS) is capable of provisioning systems back to Intel AMT 2.X. For more information about the Intel SCS and provisioning methods as they pertain to the various Intel AMT Releases, visit the download page: Download the latest version of Intel® Setup and Configuration Service (Intel® SCS)
3 Manual Configuration Tips
Since the 6.0 release, there are no feature limitations when configuring a platform manually, but there are some system behaviors to be noted:
- API methods will not return a PT_STATUS_INVALID_MODE status, as there is only one mode.
- TLS is disabled by default and should be explicitly enabled during configuration. This will always be the case with manual configuration, as there is no way to set TLS parameters locally.
- The local platform clock will be used until the network time is set remotely. Automatic configuration will not complete successfully unless the network time was set (and this can be done only when TLS or Kerberos was configured). Enabling TLS or Kerberos after configuration completion will not succeed if the network time was not set.
- WEB UI is enabled by default, unless a configuration server disables it.
- SOL and IDE-R are enabled by default, but the redirection listener is disabled by default.
- If KVM is enabled locally via the MEBx, it still will not be enabled until an administrator activates it over the network.
3.1 Manual Setup
During power up, the Intel AMT platform first displays the BIOS startup screen, and then the BIOS Extensions are processed. Entry into the Intel AMT BIOS Extension is BIOS vendor dependent. Some OEM platforms display a screen prompting you to press <Ctrl+P>. When you press <Ctrl+P>, control passes to the Intel ME BIOS extension (Intel MEBx) Main Menu. Some OEMs integrate the Intel MEBx configuration inside the BIOS, and some OEMs have an option in the BIOS to show/hide the <Ctrl+P> prompt.
4 Client Control Mode and Admin Control Mode
When any method of setup completes, Intel AMT 7.0 and later versions are placed into one of two control modes:
- Client Control Mode – Intel AMT enters this mode after performing a basic host-based setup (see Host-Based (Local) Setup). This mode limits some of Intel AMT functionality, reflecting the lower level of trust required to complete a host-based setup.
- Admin Control Mode – After performing any of the existing setup and configuration methods—remote setup (TLS-PSK or remote configuration) or a manual setup via the Intel MEBx—Intel AMT enters Admin Control Mode. Also, performing a host-based AdminSetup before any provisioning is done or an UpgradeClientToAdmin when Intel AMT is already in Client Control mode moves Intel AMT to Admin Control mode. In this mode, there are no limitations to Intel AMT functionality. This reflects the higher level of trust associated with these setup methods.
4.1 Client Control Mode Limitations
When a simple host-based configuration completes, the platform enters Client Control Mode, which imposes the following limitations:
- The System Defense feature is not available.
- Redirection (IDE-R and KVM) actions (except initiation of an SOL session) and changes in boot options (including boot to SOL) require user consent in advance. This still enables IT support personnel to remotely resolve end-user problems using Intel AMT.
- If an Auditor user is defined, the Auditor’s permission is not required to perform unprovisioning.
- A number of functions are blocked from execution to prevent an untrusted user from taking over control of the platform.
4.2 Manually Configuring an Intel AMT 9.0 Client
During power up, the Intel AMT platform first displays the BIOS startup screen, and then the BIOS Extensions are processed. Entry into the Intel AMT BIOS Extension is BIOS vendor dependent. Intel AMT reference platforms display a screen prompting you to press <Ctrl+P>. When you press <Ctrl+P>, control passes to the Intel Management Engine BIOS extension (Intel MEBx) Main Menu.
To manually set up an Intel AMT client, perform these steps:
- Enter the Intel MEBx default password (“admin”).
- Change the default password to a new value (this step is required in order to proceed). The new value must be a “strong” password. It should contain at least one upper case letter, one lower case letter, one digit and one special character, and be at least eight characters. A management console application can change the Intel AMT password without modifying the Intel MEBx password.
- Select Intel(R) AMT Configuration.
- Select Manageability Feature Selection.
- Select ENABLED to enable Intel(R) AMT.
- Select SOL/IDE-R/KVM and enable all of these features. Enabling Legacy Redirection Mode ensures compatibility with management consoles created to work with the legacy SMB mode that did do not have a mechanism implemented to enable the listener. Note that if SOL/IDER/KVM features are not enabled in the Intel MEBx they will not be available to Management Consoles.
- Select User Consent
- Select desired options for KVM and Remote IT operations. Enabling User consent means that anytime the Intel AMT Client is to be accessed remotely the user will need to agree.
- Enter Network Setup to enter network preferences for the Intel ME.
- Enter Activate Network Access to enable Intel AMT.
- Exit to the Main Menu.
- Select MEBx Exit to continue booting your system.
The platform is now configured. You can set some additional parameters using the Web User Interface (Web UI) or a remote console application.
Note that configuring the Intel AMT Client via the Intel MEBx menus will result in the system being in Admin Control Mode.
5 Accessing Intel AMT via the Web UI Interface
6 Intel AMT Drivers and Services
An administrator with user rights can remotely connect to the Intel AMT device via the Web UI by entering the IP address and one of the following port numbers into the address bar of the web browser:
- 16992 – Use if TLS is NOT configured (use http)
- 16993 – Use if TLS is configured (use https)
For example: http://134.134.176.1:16992
The Intel AMT device can also be addressed using the device’s fully qualified domain name (FQDN). If using TLS, Intel recommends using the Intel AMT FQDN instead of the IP.
For example: https://amtsystem.domain.com:16993
The following web browsers have been validated and can be used remotely to connect to any configured Intel AMT system.
- Microsoft Internet Explorer* 6.0 SP1 or later
- Netscape* 7.2 or later for Windows* and Linux*
- Mozilla* Firefox* 1.0 or newer for Windows and Linux
- Mozilla 1.7 or later for Windows and Linux
In addition to having the BIOS and ME extensions set up correctly, there are also drivers and services to be installed and running in order to fully utilize Intel AMT once it has been properly configured. To verify that the Intel AMT drivers and services are loaded correctly, look for them in the host operating systems’ Device Manger and Services. Note that every Intel AMT system should have a CD that includes all of the required firmware and drivers. Be sure to check the OEM’s download site frequently for upgraded versions of the BIOS, firmware, and drivers.
Here is a list of drivers and services that should appear in the host operating system:
- Intel® Ethernet Network Connection i217-LM#
- Intel® Centrino® Advanced-N 6205 AGN#
- Intel Management Engine Interface
- Serial-Over-LAN (SOL) Driver
- Intel® AMT LMS Service
- Intel® AMT Management and Security Status Service
# Network controller and wireless interface versions will vary depending on the generation of Intel vPro platform.
Note: The version level of the drivers must match the version level of the firmware and BIOS. If non-compatible versions are installed, Intel AMT will not work with the features that require those interfaces.
6.1 NIC: Intel Ethernet Connection
If you are wanting to check your system for Intel® AMT capability, the following network adapter needs to be present: Intel® Ethernet Network Connection i217-LM.
6.2 Intel® Management Engine Interface
Intel AMT 9.0, the platform will require a 9.x version of the MEFirmware and Driver.
6.3 Serial-Over-LAN (SOL) Driver
The system should also have the SOL drivers listed in the Device Manager.
6.4 Intel Active Management Technology LMS Service
The Local Manageability Service (LMS) runs locally in an Intel AMT device and enables local management applications to send requests and receive responses to and from the device. The LMS listens for and intercepts requests directed to the Intel AMT local host and routes them to the Intel ME via the Intel ME Interface driver.
For Intel AMT 9.0, the User Notification Service is combined with the Local Management Service.
6.5 Intel AMT User Notification Service (Pre Intel AMT 9.0)
The User Notification Service (UNS) is a Windows service installed on the host platform with Intel AMT Release 2.5 or greater. The UNS registers with the Intel AMT device to receive a set of alerts. When UNS receives an alert, it logs the alert in the Windows “Application” event log. The Event Source will be “Intel(R) AMT.”
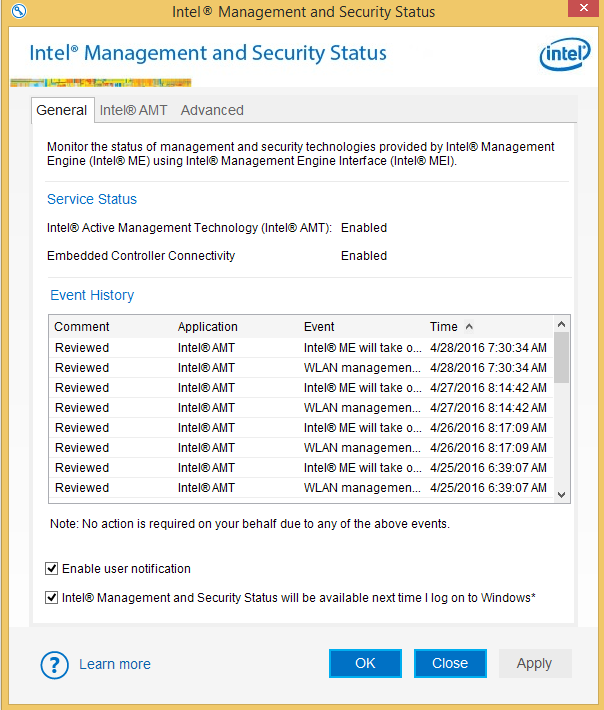
6.6 Intel Management and Security Status Tool
The Intel Management and Security Status (IMSS) tool can be accessed by the “blue key” icon in the Windows tray.

The General tab of the IMSS tool shows the status of Intel vPro services available on the platform and an event history. There are tabs for additional details of each.

Note that in the above screen shot, the system time was not set (AMT 9.0 did not exist in 2001). In order for Intel AMT to work correctly, it is important that the time be set. If there is a huge time difference between the system time and the AMT time, the firmware will “think” the system is under attack.
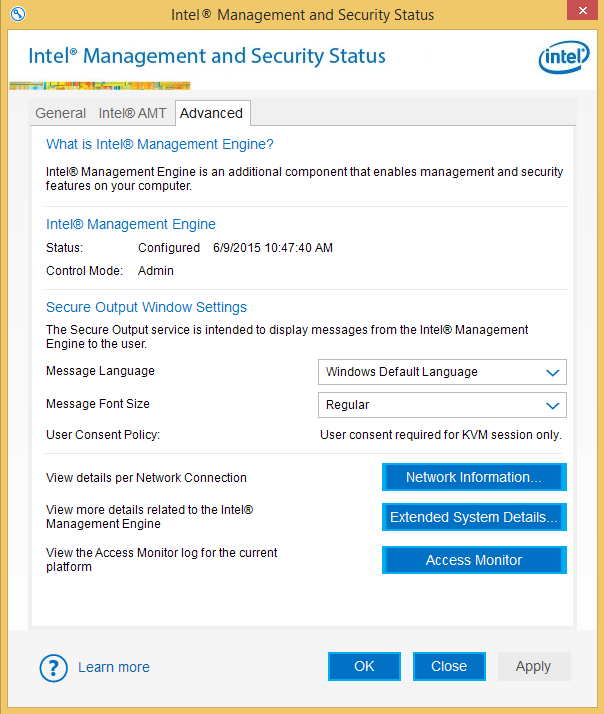
The Advanced tab of the IMSS tool shows more detailed information on the configuration of Intel AMT and its features. The following screen shot verifies that Intel AMT has been configured on this system.
7 Intel AMT Software Development Kit (SDK)
The Intel® AMT Software Development Kit (SDK) provides the low-level programming capabilities to enable developers to build manageability applications that take full advantage of Intel AMT.
The Intel AMT SDK provides sample code and a set of application programming interfaces (APIs) that let developers easily and quickly incorporate Intel AMT support into their applications. The SDK also has a full set of documentation. The SDK supports C++ and C# on Microsoft Windows and Linux operating systems. Refer to the User Guide and the Readme files in each directory for important information on building the samples. Also see the video tutorials Introduction to Intel® AMT SDK and How to compile Intel® AMT SDK sample code.
The SDK is delivered as a set of directories that can be copied to a location of the developer's choice on the development system. Because of interdependencies between components, the directory structure should be copied in its entirety. There are three folders at the top level: one called DOCS (which contains SDK documentation), and one each for Linux and Windows (which contain all of the sample code.) For more information regarding how to get started and how to use the SDK, see the "Intel® AMT Implementation and Reference Guide.”
Below is a screen shot of the Intel AMT Implementation and Reference Guide. For more information on system requirements and how to build the sample code, read through the “Using the Intel® AMT SDK” section. The documentation is available on the Intel® Software Network here: Intel® AMT SDK (Latest Release)
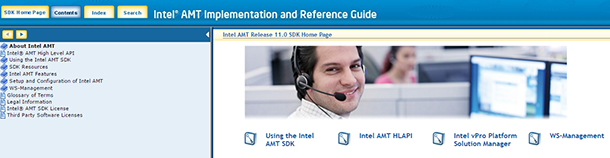
7.1 Other Intel AMT SDK Resources
The Intel AMT SDK provides frameworks and samples that simplify WS-Management development and demonstrates how to take advantage of the advanced product features. For more information, see the following:
- High Level API
- Intel vPro Platform Solution Manager
- KVM Application Developer’s Guide
- Redirection Library
- C++ CIM Framework API
- C# CIM Framework API
- WS-Management Clients Supporting C# and C++ Development
- Intel ME WMI Provider
- Management Presence Server Sample
- Posture Validation (NAC)
- System Health Validation (NAP)
- User Consent Tool
There are a variety of development environments for which to write software that supports Intel AMT. Please see the figure below for more details.
Intel® vPro Enablement Tools
- Available only in C++ (C# wrapper in SDK)
- COM object by MSFT
- Not just .NET
Appendix A:
The following table provides a snapshot of features supported by Intel AMT Releases 7, 8, and 9.
The two major changes with Intel AMT 9.0 are the addition of the Graceful Shutdown feature and the SOAP API has been deprecated in favor of the WS-Management API. In the AMT 9.0 release, SOAP support has been completely removed from the SDK.
Read about all the features in the Intel AMT SDK Implementation and Reference Guide (“Intel AMT Features” section.)
| Hardware Inventory | X | X |
| Persistent ID | X | X |
| Remote Power On/Off | X | X |
| SOL/IDER | X | X |
| Event Management | X | X |
| 3rd Party Data Storage | X | X |
| Built-in Web Server | X | X |
| Flash Protection | X | X |
| Firmware Update | X | X |
| HTTP Digest/ TLS | X | X |
| Static and Dynamic IP | X | X |
| System Defense | X | X |
| Agent Presence | X | X |
| Power Policies | X | X |
| Mutual Authentication | X | X |
| Kerberos | X | X |
| TLS-PSK | X | X |
| Privacy Icon | X | X |
| Intel® ME Wake-on-LAN | X | X |
| Remote Configuration | X | X |
| Wireless Configuration | X | X |
| Endpoint Access Control (EAC) 802.1 | X | X |
| Power Packages | X | X |
| Environment Detection | X | X |
| Event Log Reader Realm | X | X |
| System Defense Heuristics | X | X |
| WS-MAN Interface | X | X |
| VLAN settings for Intel AMT network interfaces | X | X |
| Fast Call For Help (CIRA) | X | X |
| Access Monitor | X | X |
| Microsoft NAP* Support | X | X |
| Virtualization Support for Agent Presence | X | X |
| PC Alarm Clock | X | X |
| KVM Remote Control | X | X |
| Wireless Profile Synchronization | X | X |
| Support for Internet Protocol Version 6 | X | X |
| Host Based Provisioning | X | X |
| Graceful Shutdown | X |
About the Author
Gael Hofemeier earned her BS in Math/Computer Science and an MBA from the University of New Mexico and has over 20 years of engineering experience. Gael started her career with Intel in 2000 and has been working with Intel® vPro™ technology since 2006.
Any software source code reprinted in this document is furnished under a software license and may only be used or copied in accordance with the terms of that license.
Intel, the Intel logo, and vPro are trademarks of Intel Corporation in the U.S. and/or other countries. Copyright © 2013 Intel Corporation. All rights reserved. *Other names and brands may be claimed as the property of others. [i] Intel® vPro™ Technology is sophisticated and requires setup and activation. Availability of features and results will depend upon the setup and configuration of your hardware, software and IT environment. To learn more visit: http://www.intel.com/technology/vpro.
i Requires activation and a system with a corporate network connection, an Intel® AMT-enabled chipset, network hardware and software. For notebooks, Intel AMT may be unavailable or limited over a host OS-based VPN, when connecting wirelessly, on battery power, sleeping, hibernating or powered off. Results dependent upon hardware, setup and configuration. For more information, visit Intel® Active Management Technology.
*No product or component can be absolutely secure.