Intel® AMT Basic Concepts
Passwords
Intel AMT has two commonly used passwords, they are listed below:
- Intel® Active Management Technology (Intel® AMT) Converged Security and Management Engine (CSME) Password - This password can be thought of as the physical access password, as it is only used when you are physically at the system and accessing the Intel CSME during the Boot Process. This password can be changed during access via the Intel CSME BIOS extensions, USB Configuration or remote configuration. The password character string length should be 8-32, should contain at least one upper-case letter, one lower-case letter, one digit, and one special character.
- Note: The Intel CSME is the new version of what was previously the Intel® Management Engine BIOS Extension (MEBX). This changed with the deployment of Intel AMT 11.
- The Intel AMT Admin Digest User Password - This password is the default admin password that is used for all remote connections to the Intel AMT firmware. During initial provisioning, this password is usually set as the same value as the Intel MEBX password (stored as two separate values). The password character string length should be 8-32, should contain at least one upper-case letter, one lower-case letter, one digit, and one special character.
There are three more optional passwords.
- The RFB 5900 Password - This password is required if you have configured Intel AMT to use a traditional VNC client using port 5900 for Intel® KVM Remote Control access. This password must be exactly 8 characters and should contain at least one upper-case letter, one lower-case letter, one digit, and one special character.
- Intel AMT Digest Master Password (DMP) – This is a single password that is synchronized by the IT administrator among the various management software applications. The protocol defines a method for deriving the Intel AMT administrator password from the DMP that creates a unique password per device. Using this method, the software application does not need to maintain the password database. It simplifies using multiple applications from multiple vendors to manage the Intel AMT device. You can read more about this in the Intel AMT Implementation and Reference Guide.
- Active Directory User Passwords – With Intel AMT, we can add Active Directory Users in the configuration profile as part of the Access Control List.
Configuration Types
As of Intel AMT 7, there are two types of configuration: Remote Configuration and Host-based Configuration. Both configuration options have benefits and drawbacks.
- Remote Configuration - This requires a configuration server such as Intel® Setup and Configuration Software (Intel® SCS) that hosts a special configuration certificate and profiles that are used to configure the Intel AMT firmware. This method is used primarily within enterprise networks and requires a configuration certificate as well as specific network requirements.
- Advantages: Configures devices into Admin Control Mode. This configuration method requires a SCS-type server and a purchased provisioning certificate.
- Host-based Configuration: This is for when the Host OS pushes the configuration profile to the firmware.
- Advantages: Configures devices into User Control Mode, which is less complicated to set up. User Consent is required for redirection operations, such as KVM access.
Intel® AMT Control Modes
The configuration process used will set the Intel AMT device in one of two modes: Client Control Mode (CCM) or Admin Control Mode (ACM). The difference is primarily that CCM requires "User Consent" for redirection operations (see below for details). With ACM the "User Consent" feature is available but not required.
- Client Control Mode: This is achieved when the configuration process utilizes Host-based Configuration, such as when using the Intel AMT Configuration Utility, which is a part of the Intel SCS download.
- Admin Control Mode: This is achieved when the technician has either physical access to the Intel AMT device or a configuration server such as Intel® SCS or MeshCentral, with a purchased third-party configuration certificate. ACM can be achieved by utilizing one of three configuration methods.
- Manual Configuration - This is a manual process of entering the Intel CSME of the Intel AMT client. This is usually performed by hitting CTRL+P while booting the device.
- USB Configuration – This requires booting the device to a USB Key with a setup.bin file on it. This file is created with ACUWizard or ACUConfig.
- Remote Configuration - As described above.
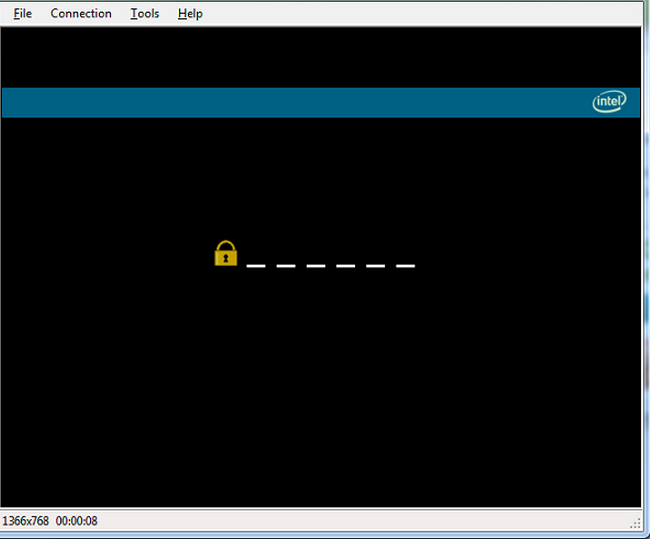
User Consent
The User Consent feature adds another level of security for remote users. When redirection is required of the remote client, a User Consent code must be submitted. Accessing an Intel AMT device via the Intel KVM Remote Control feature or executing a boot for IDE-redirect or USB-redirect are considered redirection operations, but performing a get power state or reboot is not.
The User Consent code is provided client-side as a sprite on the Intel AMT device’s display. This sprite is generated by the Intel® GPU and is not available to the OS. This is a 6-digit code that the technician will use when making the connection requiring the consent, such as an Intel KVM Connection.
*No product or component can be absolutely secure.